CS0-003 dumps are the latest exam materials for the CompTIA Cybersecurity Analyst (CySA+) exam!
leads4pass CS0-003 dumps provide 288 exam questions and answers! Our review is very strict! It fully meets the conditions for candidates to practice for the CompTIA CySA+ (CS0-003) exam, ensuring that you successfully pass the exam.
CompTIA CySA+ changes required exams:
Earn the CompTIA Cybersecurity Analyst (CySA+) certification by December 5, 2023:
You can take the CS0-002 exam or the CS0-003 exam (successfully launched on June 6, 2023).
Earn CompTIA Cybersecurity Analyst (CySA+) certification after December 5, 2023:
Take the CompTIA CySA+ CS0-003 single exam
Everything will be normal until December 5, 2023! However, if you become certified after December 5th, you will receive your new certification and associated certificates! The entire CompTIA certification ecosystem is like this. Each of their certifications can only be satisfied for three years. After three years
You will take a new exam! To learn more about CompTIA CySA+ certification, you can check the official news: https://www.comptia.org/certifications/cybersecurity-analyst
CompTIA CySA+ CS0-003 online practice exam:
| From | Number of exam questions | Related certifications |
| leads4pass | 15 Share for free | CompTIA CySA+ |
Question 1:
During a company\’s most recent incident, a vulnerability in custom software was exploited on an externally facing server by an APT. The lessons-learned report noted the following:
The development team used a new software language that was not supported by the security team\’s automated assessment tools.
During the deployment, the security assessment team was unfamiliar with the new language and struggled to evaluate the software during advanced testing.
Therefore, the vulnerability was not detected. The current IPS did not have effective signatures and policies in place to detect and prevent runtime attacks on the new application.
To allow this new technology to be deployed securely going forward, which of the following will BEST address these findings? (Choose two.)
A. Train the security assessment team to evaluate the new language and verify that best practices for secure coding have been followed
B. Work with the automated assessment tool vendor to add support for the new language so these vulnerabilities are discovered automatically
C. Contact the human resources department to hire new security team members who are already familiar with the new language
D. Run the software on isolated systems so that when they are compromised, the attacker cannot pivot to adjacent systems
E. Instruct only the development team to document the remediation steps for this vulnerability
F. Outsource development and hosting of the applications in the new language to a third-party vendor so the risk is transferred to that provider
Correct Answer: AB
Question 2:
Which of the following would help to minimize human engagement and aid in process improvement in security operations?
A. OSSTMM
B. SIEM
C. SOAR
D. QVVASP
Correct Answer: C
SOAR stands for security orchestration, automation, and response, which is a term that describes a set of tools, technologies, or platforms that can help streamline, standardize, and automate security operations and incident response processes and tasks.
SOAR can help minimize human engagement and aid in process improvement in security operations by reducing manual work, human errors, response time, or complexity. SOAR can also help enhance collaboration, coordination, efficiency, or effectiveness of security operations and incident response teams.
Question 3:
A Chief Information Security Officer (CISO) is concerned about new privacy regulations that apply to the company. The CISO has tasked a security analyst with finding the proper control functions to verify that a user\’s data is not altered without the user\’s consent. Which of the following would be an appropriate course of action?
A. Automate the use of a hashing algorithm after verified users make changes to their data.
B. Use encryption first and then hash the data at regular, defined times.
C. Use a DLP product to monitor the data sets for unauthorized edits and changes.
D. Replicate the data sets at regular intervals and continuously compare the copies for unauthorized changes.
Correct Answer: A
Automating the use of a hashing algorithm after verified users make changes to their data is an appropriate course of action” Hashing is a technique that produces a unique and fixed-length value for a given input, such as a file or a message.
Hashing can help to verify the data integrity by comparing the hash values of the original and modified data. If the hash values match, then the data has not been altered without the “lues differ, then the data may have been tampered with or corrupted.
Question 4:
A security operations manager wants some recommendations for improving security monitoring. The security team currently uses past events to create an IoC list for monitoring. Which of the following is the best suggestion for improving monitoring capabilities?
A. Update the IPS and IDS with the latest rule sets from the provider.
B. Create an automated script to update the IPS and IDS rule sets.
C. Use an automated subscription to select threat feeds for IDS.
D. Implement an automated malware solution on the IPS.
Correct Answer: C
Question 5:
Which of the following lines from this output most likely indicates that attackers could quickly use brute force and determine the negotiated secret session key?

A. TLS_RSA_WITH_DES_CBC_SHA 56
B. TLS_DHE_RSA_WITH_AES_128_CBC_SHA 128 DH (1024 bits)
C. TLS_RSA_WITH_AES_256_CBC_SHA 256
D. TLS_DHE_RSA_WITH_AES_256_GCM_SHA256 DH (2048 bits)
Correct Answer: B
The line from this output that most likely indicates that attackers could quickly use brute force and determine the negotiated secret session key is TLS_DHE_RSA_WITH_AES_128_CBC_SHA 128 DH (1024 bits).
This line indicates that the cipher suite uses Diffie-Hellman ephemeral (DHE) key exchange with RSA authentication, AES 128-bit encryption with cipher block chaining (CBC) mode, and SHA-1 hashing.
The DHE key exchange uses a 1024-bit Diffie-Hellman group, which is considered too weak for modern security standards and can be broken by attackers using sufficient computing power.
The other lines indicate stronger cipher suites that use longer key lengths or more secure algorithms. CompTIA Cybersecurity Analyst (CySA+) Certification Exam Objectives (CS0- 002), page 9; https://learn.microsoft.com/en-us/windows/win32/secauthn/cipher-suites-in-schannel
Question 6:
A company creates digitally signed packages for its devices. Which of the following best describes the method by which the security packages are delivered to the company\’s customers?
A. Antitamper mechanism
B. SELinux
C. Trusted firmware updates
D. eFuse
Correct Answer: C
Trusted firmware updates are a method by which security package” customers. Trusted firmware updates are digitally signed packages that contain software updates or patches for devices, such as routers, switches, or firewalls.
Trusted firmware updates can help to ensure the authenticity and integrity of the packages by verifying the digital signature of the sender and preventing unauthorized or malicious modifications to the packages. https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_trustsec/configuration/xe-16/sec-usr-trustsec-xe-16-book/sec-trust-firm-upd.html
Question 7:
A security analyst is monitoring a company\’s network traffic and finds ping requests going to accounting and human resources servers from an SQL server. Upon investigation, the analyst discovers a technician responded to potential network connectivity issues. Which of the following is the best way for the security analyst to respond?
A. Report this activity as a false positive, as the activity is legitimate.
B. Isolate the system and begin a forensic investigation to determine what was compromised.
C. Recommend network segmentation to the management team as a way to secure the various environments.
D. Implement host-based firewalls on all systems to prevent ping sweeps in the future.
Correct Answer: A
Reporting this activity as a false positive, as the activity is legitimate, is the best way for the security analyst to respond. A false positive is a condition in which harmless traffic is classified as a potential network attack by a security monitoring tool. Ping requests are a common network diagnostic tool that can be used to test network connectivity issues. The technician who responded to potential network connectivity issues was performing a legitimate task and did not pose any threat to the accounting and human resources servers. https://www.techopedia.com/definition39/memory-dump
Question 8:
A Chief Information Security Officer is concerned that contract developers may be able to steal the code used to design the company\’s latest application since they are able to pull code from a cloud-based repository directly to laptops that are not owned by the company. Which of the following solutions would best protect the company code from being stolen?
A. MDM
B. SCA
C. CASB
D. VDI
Correct Answer: D
VDI provides a secure environment for accessing company resources, such as code repositories, from remote locations. With VDI, the code repository would be accessed through a virtual desktop hosted on the company\’s servers, rather than on the developer\’s laptop. This means that the company\’s IT department can control the virtual desktop and ensure that it is secure, including installing security software, monitoring activity, and limiting access to the code repository.
Question 9:
A security analyst is logged on to a jump server to audit the system configuration and status. The organization\’s policies for access to and configuration of the jump server include the following:
1.
No network access is allowed to the internet.
2.
SSH is only for the management of the server.
3.
Users must utilize their own accounts, with no direct login as an administrator.
4.
Unnecessary services must be disabled.
The analyst runs Nectar with elevated permissions and receives the following output: Which of the following policies does the server violate?
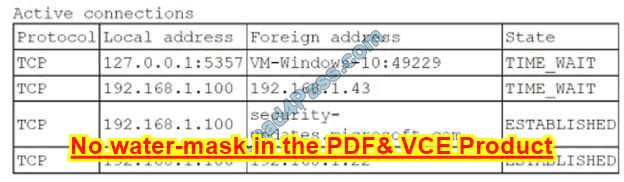
A. Unnecessary services must be disabled.
B. SSH is only for the management of the server.
C. No network access is allowed to the internet.
D. Users must utilize their own accounts, with no direct login as an administrator.
Correct Answer: C
The server violates the policy of no network access to the internet because it has an established connection to an external IP address (216.58.194.174) on port 443, which is used for HTTPS traffic. This indicates that the server is communicating with a web server on the internet, which is not allowed by the policy.
The other policies are not violated because SSH is only used for management of the server (not for accessing other devices), users are utilizing their own accounts (not logging in as an administrator), and unnecessary services are not enabled (only SSH and HTTPS are running).
CompTIA Cybersecurity Analyst (CySA+) Certification Exam Objectives (CS0-002), page 9; https://en.wikipedia.org/ wiki/Jump_server
Question 10:
A user reports a malware alert to the help desk. A technician verifies the alert, determines the workstation is classified as a low-severity device, and uses network controls to block access. The technician then assigns the ticket to a security analyst who will complete the eradication and recovery processes. Which of the following should the security analyst do next?
A. Document the procedures and walk through the incident training guide.
B. Reverse engineer the malware to determine its purpose and risk to the organization.
C. Sanitize the workstation and verify countermeasures are restored.
D. Isolate the workstation and issue a new computer to the user.
Correct Answer: C
Sanitizing the workstation and verifying countermeasures are restored are part of the eradication and recovery processes that the security analyst should perform next.
Eradication is the process of removing malware or other threats from the affected systems, while recovery is the process of restoring normal operations and functionality to the affected systems.
Sanitizing the workstation can involve deleting or wiping any malicious files or programs while verifying countermeasures are restored can involve checking and updating any security controls or settings that may have been compromised.
https://www.cynet.com/incident-response/incident-response-sans-the-6-steps-in-depth/
Question 11:
An organization wants to move non-essential services into a cloud computing environment. The management team has a cost focus and would like to achieve a recovery time objective of 12 hours. Which of the following cloud recovery strategies would work best to attain the desired outcome?
A. Duplicate all services in another instance and load balance between the instances.
B. Establish a hot site with active replication to another region within the same cloud provider.
C. Set up a warm disaster recovery site with the same cloud provider in a different region.
D. Configure the systems with a cold site at another cloud provider that can be used for failover.
Correct Answer: C
Setting up a warm disaster recovery site with the same cloud provider in a different region can help to achieve a recovery time objective (RTO) of 12 hours while keeping the costs low.
A warm disaster recovery site is a partially configured site that has some of the essential hardware and software components ready to be activated in case of a disaster.
A warm site can provide faster recovery than a cold site, which has no preconfigured components but has lower costs than a hot site, which has fully configured and replicated components.
Using the same cloud provider can help to simplify the migration and synchronization processes while using a different region can help to avoid regional outages or disasters. https://www.techopedia.com/definition39/memory-dump
Question 12:
A large company would like a security analyst to recommend a solution that will allow only company laptops to connect to the corporate network. Which of the following technologies should the analyst recommend?
A. UEBA
B. DLP
C. NAC
D. EDR
Correct Answer: C
Question 13:
A cybersecurity analyst is researching operational data to develop a script that will detect the presence of a threat on corporate assets. Which of the following contains the most useful information to produce this script?
A. API documentation
B. Protocol analysis captures
C. MITRE ATTandCK reports
D. OpenloC files
Correct Answer: C
A cybersecurity analyst is researching operational data to develop a script that will detect the presence of a threat on corporate assets.
The most useful information to produce this script is MITRE ATTandCK reports. MITRE ATTandCK is a knowledge base of adversary tactics and techniques based on real-world observations.
MITRE ATTandCK reports provide detailed information on how different threat actors operate, what tools they use, what indicators they leave behind, and how to detect or mitigate their attacks. The other options are not as useful or relevant for this purpose.
Reference: CompTIA Cybersecurity Analyst (CySA+) Certification Exam Objectives (CS0-002), page 9; https://attack.mitre.org/
Question 14:
There are several reports of sensitive information being disclosed via file-sharing services. The company would like to improve its security posture against this threat. Which of the following security controls would best support the company in this scenario?
A. Implement step-up authentication for administrators
B. Improve employee training and awareness
C. Increase password complexity standards
D. Deploy mobile device management
Correct Answer: B
The best security control to implement against sensitive information being disclosed via file-sharing services is to improve employee training and awareness.
Employee training and awareness can help educate employees on the risks and consequences of using file-sharing services for sensitive information, as well as the policies and procedures for handling such information securely and appropriately.
Employee training and awareness can also help foster a security culture and encourage employees to report any incidents or violations of information security.
Question 15:
A technician identifies a vulnerability on a server and applies a software patch. Which of the following should be the next step in the remediation process?
A. Testing
B. Implementation
C. Validation
D. Rollback
Correct Answer: C
The next step in the remediation process after applying a software patch is validation. Validation is a process that involves verifying that the patch has been successfully applied, that it has fixed the vulnerability, and that it has not caused any adverse effects on the system or application functionality or performance. Validation can be done using various methods, such as scanning, testing, monitoring, or auditing.
…
Summarize:
CompTIA CySA+ certification will be updated every three years! leads4pass CS0-003 dumps are the latest exam materials serving the CompTIA CySA+ certification exam!
Candidates use CS0-003 dumps with PDF and VCE: https://www.leads4pass.com/cs0-003.html (288 Q&A) to help them practice the test easily and pass the exam with 100% success.