
CompTIA CAS-004 dumps 2024 is the latest exam material for the CompTIA Advanced Security Practitioner (CASP+) exam!
CompTIA CAS-004 dumps 2024 exam solution developed based on core exam questions, including 521 latest exam questions and answers! Provides two exam practice methods, PDF and VCE!
Download the CompTIA CAS-004 dumps 2024 provided by Leads4pass, the CompTIA exam material center: https://www.leads4pass.com/cas-004.html to ensure you pass the exam successfully on the first try.
Provides the latest CompTIA CAS-004 dumps 2024 online exam practice:
| From | Number of exam questions | Related Certification Exam Questions | Type |
| Leads4Pass (leads4pass 2023) | 15 | CompTIA Advanced Security Practitioner (CASP+) | Free |
Question 1:
A security architect for a large, multinational manufacturer needs to design and implement a security solution to monitor traffic.
When designing the solution, which of the following threats should the security architect focus on to prevent attacks against the network?
A. Packets that are the wrong size or length
B. Use of any non-DNP3 communication on a DNP3 port
C. Multiple solicited responses over time
D. Application of an unsupported encryption algorithm
Correct Answer: B
Question 2:
A security engineer is working for a service provider and analyzing logs and reports from a new EDR solution, which is installed on a small group of workstations. Later that day, another security engineer receives an email from two developers reporting the software being used for development activities is now blocked. The developers have not made any changes to the software being used. Which of the following is the EDR reporting?
A. True positive
B. False negative
C. False positive
D. True negative
Correct Answer: C
Question 3:
A security analyst is concerned that a malicious piece of code was downloaded on a Linux system. After some research, the analyst determines that the suspected piece of code is performing a lot of input/output (I/O) on the disk drive.
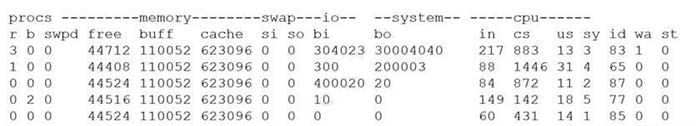
Based on the output above, from which of the following process IDs can the analyst begin an investigation?
A. 65
B. 77
C. 83
D. 87
Correct Answer: C
Question 4:
A local university that has a global footprint is undertaking a complete overhaul of its website and associated systems Some of the requirements are:
1.
Handle an increase in customer demand of resources
2.
Provide quick and easy access to information
3.
Provide high-quality streaming media
4.
Create a user-friendly interface
Which of the following actions should be taken FIRST?
A. Deploy high-availability web servers.
B. Enhance network access controls.
C. Implement a content delivery network.
D. Migrate to a virtualized environment.
Correct Answer: C
Question 5:
A security analyst is trying to identify the source of a recent data loss incident The analyst has reviewed all the logs for the time surrounding the incident and identified all the assets on the network at the time of the data loss. The analyst suspects the key to finding the source was obfuscated in an application.
Which of the following tools should the analyst use NEXT?
A. Software decompiler
B. Network enumerator
C. Log reduction and analysis tool
D. Static code analysis
Correct Answer: D
Question 6:
A small business would like to provide guests who are using mobile devices encrypted WPA3 access without first distributing PSKs or other credentials. Which of the following features will enable the business to meet this objective?
A. Simultaneous Authentication of Equals
B. Enhanced open
C. Perfect forward secrecy
D. Extensible Authentication Protocol
Correct Answer: A
Question 7:
An attack team performed a penetration test on a new smart card system. The team demonstrated that by subjecting the smart card to high temperatures, the secret key could be revealed. Which of the following side-channel attacks did the team use?
A. Differential power analysis
B. Differential fault analysis
C. Differential temperature analysis
D. Differential timing analysis
Correct Answer: B
“Differential fault analysis (DFA) is a type of active side-channel attack in the field of cryptography, specifically cryptanalysis. The principle is to induce faults–unexpected environmental conditions–into cryptographic operations, to reveal their internal states.”
Reference: https://www.hitachi-hightech.com/global/products/science/tech/ana/thermal/descriptions/dta.html
Question 8:
A company is acquiring a competitor, and the security team is performing due diligence activities on the competitor before the acquisition. The team found a recent compliance audit of the competitor\’s environment that shows a mature security infrastructure, but it lacks a cohesive policy and process framework. Based on the audit findings, the security team determines the competitor\’s existing security capabilities are sufficient, but they will need to incorporate additional security policies. Which of the following risk management strategies is the security team recommending?
A. Mitigate and avoid
B. Transfer and accept
C. Avoid and transfer
D. Accept and mitigate
Correct Answer: D
The security team accepts the risk that the competitor\’s existing security policies and procedures are not comprehensive enough. However, the team is also mitigating this risk by implementing additional security policies.
Question 9:
An organization collects personal data from its global customers. The organization determines how that data is going to be used, why it is going to be used, and how it is manipulated for business processes. Which of the following will the organization need to comply with GDPR? (Choose two.)
A. Data processor
B. Data custodian
C. Data owner
D. Data steward
E. Data controller
F. Data manager
Correct Answer: AE
Question 10:
A new, online file hosting service is being offered. The service has the following security requirements:
1.
Threats to customer data integrity and availability should be remediated first.
2.
The environment should be dynamic to match increasing customer demands.
3.
The solution should not interfere with customers\’ ability to access their data at any time.
4.
Security analysts should focus on high-risk items.
Which of the following would BEST satisfy the requirements?
A. Expanding the use of IPS and NGFW devices throughout the environment
B. Increasing the number of analysts to identify risks that need remediation
C. Implementing a SOAR solution to address known threats
D. Integrating enterprise threat feeds in the existing SIEM
Correct Answer: C
Question 11:
In a cloud environment, the provider offers relief to an organization\’s teams by sharing in many of the operational duties. In a shared responsibility model, which of the following responsibilities belongs to the provider in a PaaS implementation?
A. Application-specific data assets
B. Application user access management
C. Application-specific logic and code
D. Application/platform software
Correct Answer: D
Question 12:
A security engineer is creating a single CSR for the following web server hostnames:
1.
wwwint.internal
2.
www.company.com
3.
home.internal
4.
www.internal
Which of the following would meet the requirement?
A. SAN
B. CN
C. CA
D. CRL
E. Issuer
Correct Answer: A
Question 13:
A security engineer is hardening a company\’s multihomed SFTP server. When scanning a public-facing network interface, the engineer finds the following ports are open:
1.
22
2.
25
3.
110
4.
137
5.
138
6.
139
7.
445
Internal Windows clients are used to transferring files to the server to stage them for customer download as part of the company\’s distribution process.
Which of the following would be the BEST solution to harden the system?
A. Close ports 110, 138, and 139. Bind ports 22, 25, and 137 to only the internal interface.
B. Close ports 25 and 110. Bind ports 137, 138, 139, and 445 to only the internal interface.
C. Close ports 22 and 139. Bind ports 137, 138, and 445 to only the internal interface.
D. Close ports 22, 137, and 138. Bind ports 110 and 445 to only the internal interface.
Correct Answer: B
Question 14:
An investigator is attempting to determine if recent data breaches may be due to issues with a company\’s web server that offers news subscription services. The investigator has gathered the following data:
1.
Clients successfully establish TLS connections to web services provided by the server.
2.
After establishing the connections, most client connections are renegotiated.
3.
The renegotiated sessions use the cipher suite TLS_RSA_WITH_NULL_SHA.
Which of the following is the MOST likely root cause?
A. The clients disallow the use of modem cipher suites.
B. The web server is misconfigured to support HTTP/1.1
C. A ransomware payload dropper has been installed.
D. An entity is performing downgrade attacks on the path.
Correct Answer: D
Question 15:
A recent data breach stemmed from unauthorized access to an employee\’s company account with a cloud-based productivity suite. The attacker exploited excessive permissions granted to a third-party OAuth application to collect sensitive information.
Which of the following BEST mitigates inappropriate access and permissions issues?
A. SIEM
B. CASB
C. WAF
D. SOAR
Correct Answer: B
Reference: https://www.cloudflare.com/en-gb/learning/ddos/glossary/web-application-firewall-waf/
…
The CompTIA CAS-004 Dumps exam materials provided by Leads4Pass are verified and reviewed by the CompTIA CASP+ exam expert team and meet the 2024 Comptia CASP+ exam requirements, ensuring that you pass with high scores!
Download the CompTIA CAS-004 Dumps containing 521 exam questions and answers online: https://www.leads4pass.com/cas-004.html (provides the best practice tools PDF and VCE).




