CompTIA CySA+ CS0-002 dumps have been updated to the latest version, reviewed and corrected by the CompTIA team, in line with the actual certification exam!
The CompTIA CySA+ certification (CS0-002 CompTIA CySA+ Exam) is a must-have certification to prepare you for the Cyber Security Analyst job role! Passing the CS0-002 CompTIA CySA+ Exam is very important!
Therefore, leads4pass has updated CompTIA CySA+ CS0-002 dumps, which contain 1013 latest exam questions and answers, which are real and effective exam materials!
Now, download CompTIA CySA+ CS0-002 dumps with PDF and VCE: https://www.leads4pass.com/cs0-002.html to help you study easily and pass the exam successfully.
And share a copy of CompTIA CySA+ CS0-002 dumps exam questions online practice for free
| From | Number of exam questions | Associated certification | Online Download | Last update |
| leads4pass | 13 | CompTIA CySA+ | CS0-002 PDF | CS0-002 dumps |
NEW QUESTION 1:
Organizational policies require vulnerability remediation on severity 7 or greater within one week. Anything with a severity of less than 7 must be remediated within 30 days.
The organization also requires security teams to investigate the details of a vulnerability before performing any remediation.
If the investigation determines the finding is a false positive, no remediation is performed and the vulnerability scanner configuration is updated to omit the false positive from future scans:
The organization has three Apache web servers:
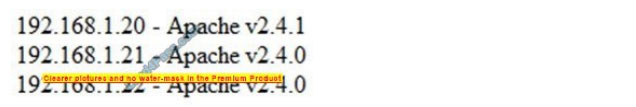
The results of a recent vulnerability scan are shown below: The team performs some investigation and finds a statement from Apache:
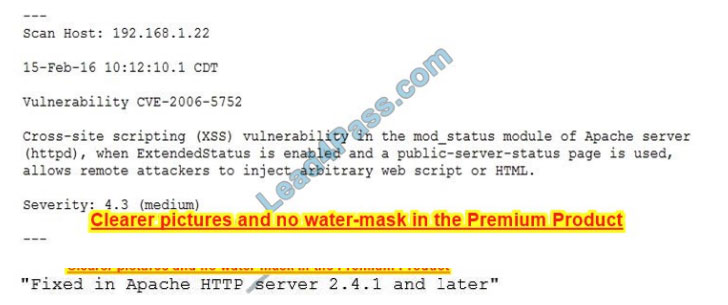
Which of the following actions should the security team perform?
A. Ignore the false positive on 192.168.1.22
B. Remediate 192.168.1.20 within 30 days
C. Remediate 192.168.1.22 within 30 days
D. Investigate the false negative on 192.168.1.20
Correct Answer: C
NEW QUESTION 2:
A Chief Information Security Officer (CISO) wants to upgrade an organization\’s security posture by improving proactive activities associated with attacks from internal and external threats.
Which of the following is the MOST proactive tool or technique that feeds incident response capabilities?
A. Development of a hypothesis as part of threat hunting
B. Log correlation, monitoring, and automated reporting through a SIEM platform
C. Continuous compliance monitoring using SCAP dashboards
D. Quarterly vulnerability scanning using credentialed scans
Correct Answer: A
NEW QUESTION 3:
A security analyst is reviewing the following web server log: GET %2f..%2f..%2f.. %2f.. %2f.. %2f.. %2f../etc/passwd Which of the following BEST describes the issue?
A. Directory traversal exploit
B. Cross-site scripting
C. SQL injection
D. Cross-site request forgery
Correct Answer: A
NEW QUESTION 4:
When network administrators observe an increased amount of web traffic without an increased number of financial transactions, the company is MOST likely experiencing which of the following attacks?
A. Bluejacking
B. ARP cache poisoning
C. Phishing
D. DoS
Correct Answer: D
NEW QUESTION 5:
Which of the following sources will provide the MOST relevant threat intelligence data to the security team of a dental care network?
A. H-ISAC
B. Dental forums
C. Open threat exchange
D. Dark web chatter
Correct Answer: A
Reference: https://h-isac.org/
NEW QUESTION 6:
A cybersecurity analyst is supposing an incident response effort via threat intelligence. Which of the following is the analyst MOST likely executing?
A. Requirements analysis and collection planning
B. Containment and eradication
C. Recovery and post-incident review
D. Indicator enrichment and research pivoting
Correct Answer: D
NEW QUESTION 7:
An alert is issued from the SIEM that indicates a large number of failed logins for the same account name on one of the application servers starting at 10:20 a.m.
No other significant failed login activity is detected.
Using Splunk to search for activity pertaining to that account name, a security analyst finds the account has been authenticating successfully for some time and started to fail this morning.
The account is attempting to authenticate from an internal server that is running a database to an application server. No other security activity is detected on the network.
The analyst discovers the account owner is a developer who no longer works for the company.
Which of the following is the MOST likely reason for the failed login attempts for that account?
A. The account that is failing to authenticate has not been maintained, and the company password change policy time frame has been reached for that account
B. The host-based firewall is blocking port 389 LDAP communication, preventing the login credentials from being received by the application server
C. The license for the application has expired, and the failed logins will continue to occur until a new license key is installed on the application
D. A successful malware attack has provided someone access to the network, and failed login attempts are an indication of an attempt to privilege access to the application
Correct Answer: A
NEW QUESTION 8:
A security analyst is reviewing IDS logs and notices the following entry:

Which of the following attacks is occurring?
A. Cross-site scripting
B. Header manipulation
C. SQL injection
D. XML injection
Correct Answer: C
NEW QUESTION 9:
A cybersecurity analyst has received a report that multiple systems are experiencing slowness as a result of a DDoS attack. Which of the following would be the BEST action for the cybersecurity analyst to perform?
A. Continue monitoring critical systems.
B. Shut down all server interfaces.
C. Inform management of the incident.
D. Inform users regarding the affected systems.
Correct Answer: C
NEW QUESTION 10:
A security analyst is looking at the headers of a few emails that appear to be targeting all users at an organization:
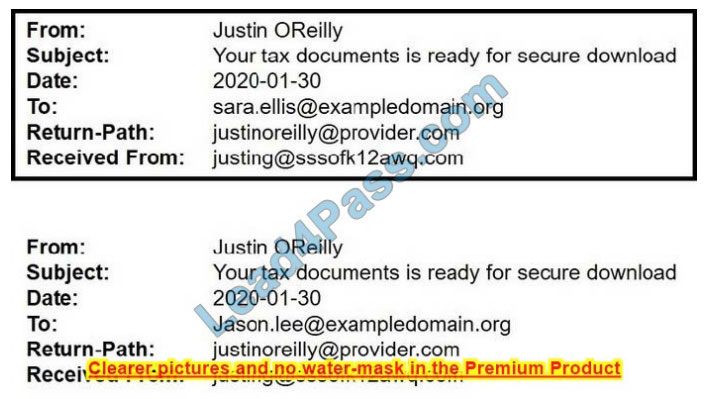
Which of the following technologies would MOST likely be used to prevent this phishing attempt?
A. DNSSEC
B. DMARC
C. STP
D. S/IMAP
Correct Answer: B
Reference: https://dmarc.org/
NEW QUESTION 11:
Some hard disks need to be taken as evidence for further analysis during an incident response.
Which of the following procedures must be completed FIRST for this type of evidence acquisition?
A. Extract the hard drives from the compromised machines and then plug them into a forensics machine to apply encryption over the stored data to protect it from non-authorized access
B. Build the chain-of-custody document, noting the media model serial number size vendor, date, and time of acquisition
C. Perform a disk sanitation using the command 8dd if=/d/zo of=/d/c b? I’m over the media that will receive a copy of the collected data
D. Execute the command #dd if=/dev/ada of=/dev/adc ba=5i2 to clone the evidence data to external media to prevent any further change
Correct Answer: B
NEW QUESTION 12:
An organization is upgrading its network and all of its workstations. The project will occur in phases, with infrastructure upgrades each month and workstation installs every other week.
The schedule should accommodate the enterprise-wide changes while minimizing the impact on the network.
Which of the following schedules BEST addresses these requirements?
A. Monthly vulnerability scans, biweekly topology scans, daily host discovery scans
B. Monthly topology scans, biweekly host discovery scans, monthly vulnerability scans
C. Monthly host discovery scans, biweekly vulnerability scans, monthly topology scans
D. Monthly topology scans, biweekly host discovery scans, weekly vulnerability scans
Correct Answer: B
NEW QUESTION 13:
As part of an organization\’s information security governance process, a Chief Information Security Officer (CISO) is working with the compliance officer to update policies to include statements related to new regulatory and legal requirements.
Which of the following should be done to BEST ensure all employees are appropriately aware of changes
to the policies?
A. Conduct a risk assessment based on the controls defined in the newly revised policies
B. Require all employees to attend updated security awareness training and sign an acknowledgment
C. Post the policies on the organization\’s intranet and provide copies of any revised policies to all active vendors
D. Distribute revised copies of policies to employees and obtain a signed acknowledgment from them
Correct Answer: B
…
The CompTIA CySA+ certification is a certification for network professionals tasked with incident detection, prevention, and response through continuous security monitoring! The condition is to successfully pass the CS0-002 CompTIA CySA+ Exam!
Participating in the online practice of CompTIA CySA+ CS0-002 dumps exam questions can help you learn more practical and useful exam skills and improve your exam pass rate! The CompTIA CySA+ CS0-002 dumps with PDF and VCE are now recommended:
https://www.leads4pass.com/cs0-002.html helps you pass the exam 100% successfully.