
If you’re preparing for the CompTIA SecurityX (formerly CASP+) CAS-005 certification exam, you’re in the right place. Use the latest CAS-005 dumps from Leads4Pass to practice effectively. Our fully updated CAS-005 dumps include 261 of the latest exam questions and answers to help you pass with ease.
Get the latest CAS-005 dumps at https://www.leads4pass.com/cas-005.html. Choose from PDF or VCE advanced simulation engines to help you prepare effortlessly.
You can also take the CompTIA CAS-005 online practice tests first, which are completely free.
Latest CAS-005 Dumps: Free sharing of some exam practice questions
| Number of exam questions | Related |
| 15 (Free) | CASP+ |
Question 1:
A security technician is trying to connect a remote site to the central office over a site-to-site VPN. The technician has verified the source and destination IP addresses are correct, but the technician is unable to get the remote site to connect. The following error message keeps repeating:
An error has occurred during Phase 1 handshake. Deleting keys and retrying…
Which of the following is most likely the reason the connection is failing?
A. The IKE hashing algorithm uses different key lengths on each VPN device.
B. The IPSec settings allow more than one cipher suite on both devices.
C. The Diffie-Hellman group on both sides matches but is a legacy group.
D. The remote VPN is attempting to connect with a protocol other than SSL/TLS.
Correct Answer: C
The error message “An error has occurred during Phase 1 handshake. Deleting keys and retrying…” suggests that there is an issue with the initial negotiation or key exchange process. Legacy Diffie-Hellman groups are a common cause of such issues because modern VPN devices might reject or fail to negotiate with older, less secure groups.
Question 2:
A software developer has been tasked with creating a unique threat detection mechanism that is based on machine learning. The information system for which the tool is being developed is on a rapid CI/CD pipeline, and the tool developer is considered a supplier to the process. Which of the following presents the most risk to the development life cycle and to the ability to deliver the security tool on time?
A. Deep learning language barriers
B. Big Data processing required for maturity
C. Secure, multiparty computation requirements
D. Computing capabilities available to the developer
Correct Answer: B
Question 3:
A company that uses containers to run its applications is required to identify vulnerabilities on every container image in a private repository The security team needs to be able to quickly evaluate whether to respond to a given vulnerability.
Which of the following, will allow the security team to achieve the objective with the last effort?
A. SAST scan reports
B. Centralized SBoM
C. CIS benchmark compliance reports
D. Credentialed vulnerability scan
Correct Answer: B
A centralized Software Bill of Materials (SBoM) is the best solution for identifying vulnerabilities in container images in a private repository. An SBoM provides a comprehensive inventory of all components, dependencies, and their versions
within a container image, facilitating quick evaluation and response to vulnerabilities.
Why Centralized SBoM?
Comprehensive Inventory: An SBoM lists all software components, including their versions and dependencies, allowing for thorough vulnerability assessments. Quick Identification: Centralizing SBoM data enables rapid identification of
affected containers when a vulnerability is disclosed.
Automation: SBoMs can be integrated into automated tools for continuous monitoring and alerting of vulnerabilities.
Regulatory Compliance: Helps in meeting compliance requirements by providing a clear and auditable record of all software components used. Other options, while useful, do not provide the same level of comprehensive and efficient
vulnerability management:
A. SAST scan reports: Focuses on static analysis of code but may not cover all components in container images.
C. CIS benchmark compliance reports: Ensures compliance with security benchmarks but does not provide detailed component inventory. D. Credentialed vulnerability scan: Useful for in-depth scans but may not be as efficient for quick vulnerability evaluation.
References: CompTIA SecurityX Study Guide “Software Bill of Materials (SBoM),” NIST Documentation “Managing Container Security with SBoM,” OWASP
Question 4:
A company is having issues with its vulnerability management program New devices/lPs are added and dropped regularly, making the vulnerability report inconsistent
Which of the following actions should the company lake to most likely improve the vulnerability management process\’
A. Request a weekly report with all new assets deployed and decommissioned
B. Extend the DHCP lease lime to allow the devices to remain with the same address for a longer period.
C. Implement a shadow IT detection process to avoid rogue devices on the network
D. Perform regular discovery scanning throughout the 11 landscape using the vulnerability management tool
Correct Answer: D
To improve the vulnerability management process in an environment where new devices/IPs are added and dropped regularly, the company should perform regular discovery scanning throughout the IT landscape using the vulnerability management tool.
Here\’s why:
Accurate Asset Inventory: Regular discovery scans help maintain an up-to-date inventory of all assets, ensuring that the vulnerability management process includes all relevant devices and IPs.
Consistency in Reporting: By continuously discovering and scanning new and existing assets, the company can generate consistent and comprehensive vulnerability reports that reflect the current state of the network.
Proactive Management:
Regular scans enable the organization to proactively identify and address vulnerabilities on new and existing assets, reducing the window of exposure to potential threats.
Question 5:
A security analyst is conducting an investigation regarding a potential insider threat. An unauthorized USB device might have been used to exfiltrate proprietary data from a Linux system.
Which of the following options would identify the IoCs and provide the appropriate response?
A. Review the network logs and update the firewall rules.
B. Review the operating system logs and update the DLP rules.
C. Review the vulnerability logs and update the IDS rules.
D. Obtain the device ID using dmesg and update the portable storage inventory.
Correct Answer: B
Data visibility and endpoint DLP can secure data at-rest and ensure that users do not exfiltrate data via a removable device, such as a USB. The exercise does not specify if the DLP is a network or endpoint based.
Question 6:
SIMULATION
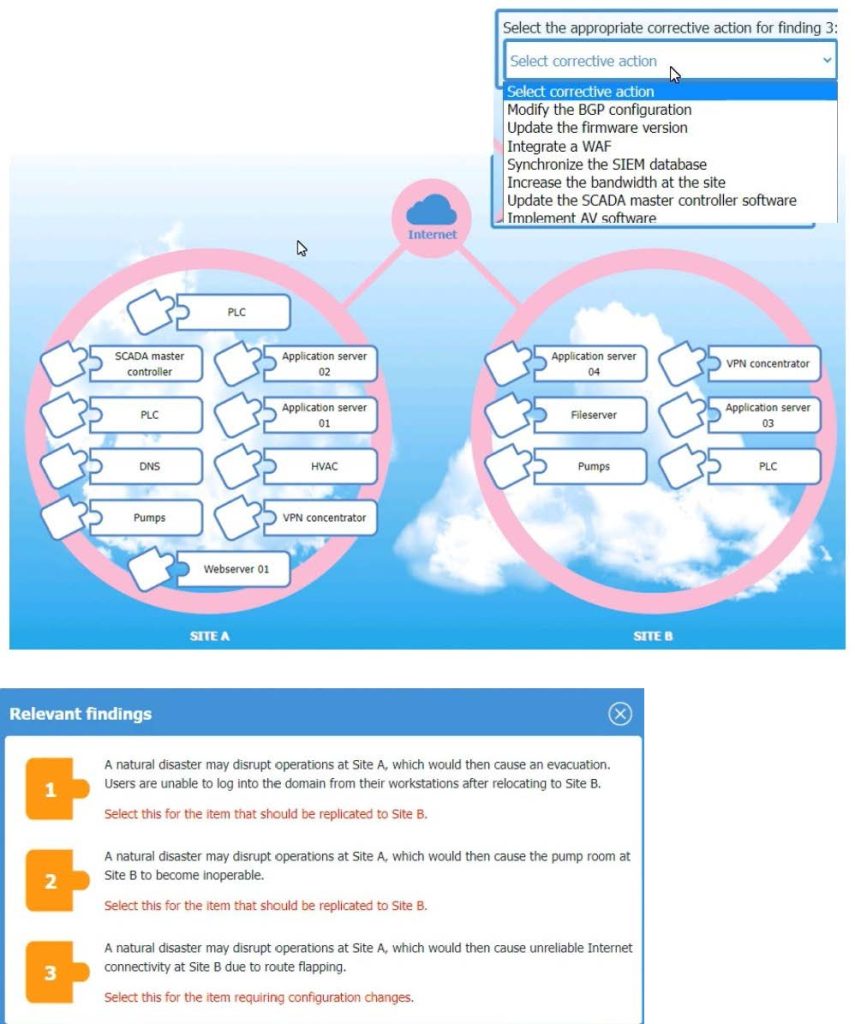
An organization is planning for disaster recovery and continuity of operations, and has noted the following relevant findings:
1.
A natural disaster may disrupt operations at Site A, which would then cause an evacuation. Users are unable to log into the domain from-their workstations after relocating to Site B.
2.
A natural disaster may disrupt operations at Site A, which would then cause the pump room at Site B to become inoperable.
3.
A natural disaster may disrupt operations at Site A, which would then cause unreliable internet connectivity at Site B due to route flapping.
INSTRUCTIONS
Match each relevant finding to the affected host by clicking on the host name and selecting the appropriate number.
For findings 1 and 2, select the items that should be replicated to Site B. For finding 3, select the item requiring configuration changes, then select the appropriate corrective action from the drop-down menu.
A. See the complete solution below in Explanation.
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
Correct Answer: A
Matching Relevant Findings to the Affected Hosts:
Finding 1:
Finding 2:
Finding 3:
Corrective Actions for Finding 3:
Finding 3 Corrective Action:
Replication to Site B for Finding 1:
Replication to Site B for Finding 2:
Configuration Changes for Finding 3:
References:
CompTIA Security+ Study Guide: This guide provides detailed information on disaster recovery and continuity of operations, emphasizing the importance of replicating critical services and making necessary configuration changes to ensure
seamless operation during disruptions.
CompTIA Security+ Exam Objectives: These objectives highlight key areas in disaster recovery planning, including the replication of critical services and network configuration adjustments.
Disaster Recovery and Business Continuity Planning (DRBCP): This resource outlines best practices for ensuring that operations can continue at an alternate site during a disaster, including the replication of essential services and network
stability measures.
By ensuring that critical services like DNS and control systems for pumps are replicated at the alternate site, and by addressing network routing issues through proper BGP configuration, the organization can maintain operational continuity
and minimize the impact of natural disasters on their operations.
Question 7:
A hospital provides tablets to its medical staff to enable them to more quickly access and edit patients\’ charts. The hospital wants to ensure that if a tablet is Identified as lost or stolen and a remote command is issued, the risk of data loss can be mitigated within seconds. The tablets are configured as follows to meet hospital policy
1.
Full disk encryption is enabled
2.
Always O”; corporate VPN is enabled
3.
ef-use-backed keystore is enabled\’ready.
4.
Wi-Fi 6 is configured with SAE.
5.
Location services is disabled.
6.
Application allow list is configured
A. Revoking the user certificates used for VPN and Wi-Fi access
B. Performing cryptographic obfuscation
C. Using geolocation to find the device
D. Configuring the application allow list to only per mil emergency calls
E. Returning on the device\’s solid-state media to zero
Correct Answer: E
To mitigate the risk of data loss on a lost or stolen tablet quickly, the most effective strategy is to return the device\’s solid-state media to zero, which effectively erases all data on the device.
Here\’s why:
Immediate Data Erasure: Returning the solid-state media to zero ensures that all data is wiped instantly, mitigating the risk of data loss if the device is lost or stolen. Full Disk Encryption: Even though the tablets are already encrypted,
physically erasing the data ensures that no residual data can be accessed if someone attempts to bypass encryption.
Compliance and Security: This method adheres to best practices for data security and compliance, ensuring that sensitive patient data cannot be accessed by unauthorized parties.
Question 8:
A security administrator is setting up a virtualization solution that needs to run services from a single host. Each service should be the only one running in its environment. Each environment needs to have its own operating system as a base but share the kernel version and properties of the running host. Which of the following technologies would best meet these requirements?
A. Containers
B. Type 1 hypervisor
C. Type 2 hypervisor
D. Virtual desktop infrastructure
E. Emulation
Correct Answer: A
Containers are the most suitable technology for the scenario described by the security administrator. They allow each service to run in its own isolated environment with its own filesystem and processes while sharing the host\’s kernel. This meets the requirement of having separate OS environments for each service but leveraging the common properties and kernel version of the host system, ensuring efficient resource utilization and isolation between services.
Question 9:
A security architect wants to develop a baseline of security configurations These configurations automatically will be utilized machine is created
Which of the following technologies should the security architect deploy to accomplish this goal?
A. Short
B. GASB
C. Ansible
D. CMDB
Correct Answer: C
To develop a baseline of security configurations that will be automatically utilized when a machine is created, the security architect should deploy Ansible.
Here\’s why:
Automation: Ansible is an automation tool that allows for the configuration, management, and deployment of applications and systems. It ensures that security configurations are consistently applied across all new machines.
Scalability:
Ansible can scale to manage thousands of machines, making it suitable for large enterprises that need to maintain consistent security configurations across their infrastructure.
Compliance: By using Ansible, organizations can enforce compliance with security policies and standards, ensuring that all systems are configured according to best practices.
Question 10:
A company has been the target of LDAP injections, as well as brute-force, whaling, and spear-phishing attacks. The company is concerned about ensuring continued system access. The company has already implemented a SSO system with strong passwords. Which of the following additional controls should the company deploy?
A. Two-factor authentication
B. Identity proofing
C. Challenge questions
D. Live identity verification
Correct Answer: A
Question 11:
Third parties notified a company\’s security team about vulnerabilities in the company\’s application. The security team determined these vulnerabilities were previously disclosed in third-party libraries.
Which of the following solutions best addresses the reported vulnerabilities?
A. Using laC to include the newest dependencies
B. Creating a bug bounty program
C. Implementing a continuous security assessment program
D. Integrating a SASI tool as part of the pipeline
Correct Answer: D
The best solution to address reported vulnerabilities in third-party libraries is integrating a Static Application Security Testing (SAST) tool as part of the development pipeline.
Here\’s why:
Early Detection: SAST tools analyze source code for vulnerabilities before the code is compiled. This allows developers to identify and fix security issues early in the development process.
Continuous Security: By integrating SAST tools into the CI/CD pipeline, the organization ensures continuous security assessment of the codebase, including third-party libraries, with each code commit and build.
Comprehensive Analysis:
SAST tools provide a detailed analysis of the code, identifying potential vulnerabilities in both proprietary code and third-party dependencies, ensuring that known issues in libraries are addressed promptly.
Question 12:
A company plans to implement a research facility with Intellectual property data that should be protected The following is the security diagram proposed by the security architect
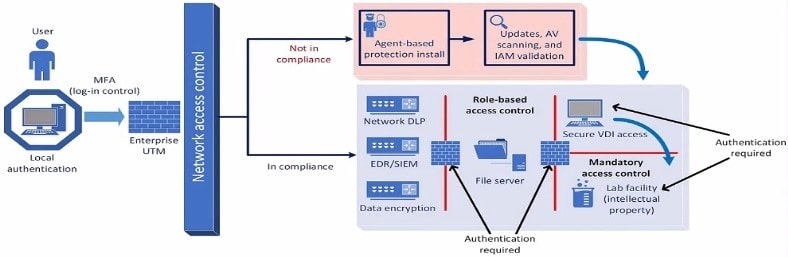
Which of the following security architect models is illustrated by the diagram?
A. Identity and access management model
B. Agent based security model
C. Perimeter protection security model
D. Zero Trust security model
Correct Answer: D
The security diagram proposed by the security architect depicts a Zero Trust security model. Zero Trust is a security framework that assumes all entities, both inside and outside the network, cannot be trusted and must be verified before gaining access to resources.
Key Characteristics of Zero Trust in the Diagram:
Role-based Access Control: Ensures that users have access only to the resources necessary for their role.
Mandatory Access Control: Additional layer of security requiring authentication for access to sensitive areas.
Network Access Control: Ensures that devices meet security standards before accessing the network.
Multi-factor Authentication (MFA): Enhances security by requiring multiple forms of verification.
This model aligns with the Zero Trust principles of never trusting and always verifying access requests, regardless of their origin.
References:
CompTIA SecurityX Study Guide
NIST Special Publication 800-207, “Zero Trust Architecture” “Implementing a Zero Trust Architecture,” Forrester Research
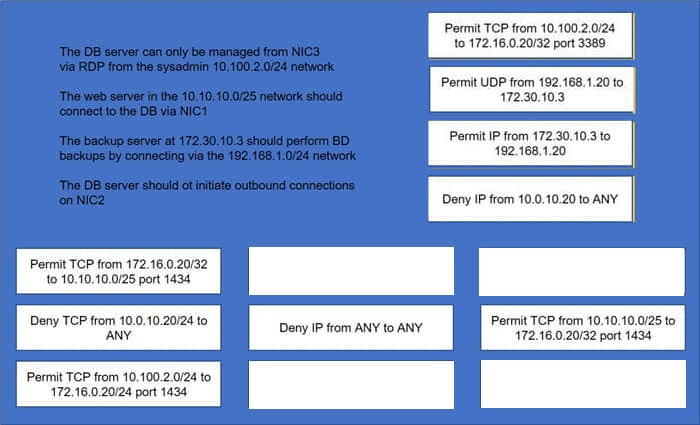
Question 13:
DRAG DROP
A security administrator must configure the database server shown below the comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.
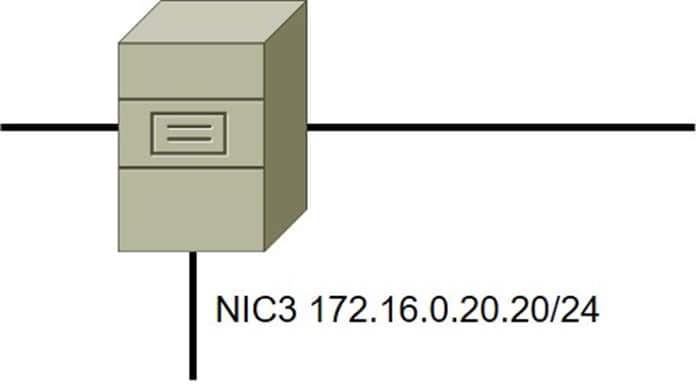
Select and Place:
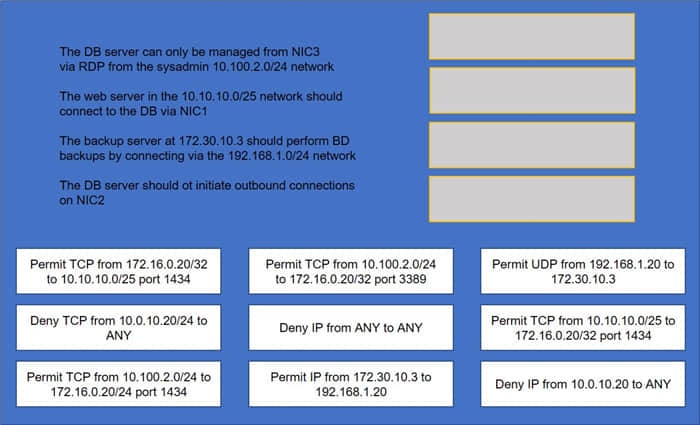
Correct Answer:
Question 14:
Emails that the marketing department is sending to customers are pomp to the customers\’ spam folders. The security team is investigating the issue and discovers that the certificates used by the email server were reissued, but DNS records had not been updated.
Which of the following should the security team update in order to fix this issue? (Select three.)
A. DMARC
B. SPF
C. DKIM
D. DNSSEC
E. SASC
F. SAN
G. SOA
H. MX
Correct Answer: ABC
To prevent emails from being marked as spam, several DNS records related to email authentication need to be properly configured and updated when there are changes to the email server\’s certificates:
A. DMARC (Domain-based Message Authentication, Reporting and Conformance):
DMARC records help email servers determine how to handle messages that fail SPF or DKIM checks, improving email deliverability and reducing the likelihood of emails being marked as spam. B. SPF (Sender Policy Framework): SPF
records specify which mail servers are authorized to send email on behalf of your domain. Updating the SPF record ensures that the new email server is recognized as an authorized sender. C. DKIM (DomainKeys Identified Mail): DKIM adds
a digital signature to email headers, allowing the receiving server to verify that the email has not been tampered with and is from an authorized sender. Updating DKIM records ensures that emails are properly signed and authenticated. D.
DNSSEC (Domain Name System Security Extensions): DNSSEC adds security to DNS by enabling DNS responses to be verified. While important for DNS security, it does not directly address the issue of emails being marked as spam. E.
SASC: This is not a relevant standard for this scenario. F. SAN (Subject Alternative Name): SAN is used in SSL/TLS certificates for securing multiple domain names, not for email delivery issues. G. SOA (Start of Authority): SOA records are
used for DNS zone administration and do not directly impact email deliverability.
H. MX (Mail Exchange): MX records specify the mail servers responsible for receiving email on behalf of a domain. While important, the primary issue here is the authentication of outgoing emails, which is handled by SPF, DKIM, and
DMARC.
References:
CompTIA Security+ Study Guide
RFC 7208 (SPF), RFC 6376 (DKIM), and RFC 7489 (DMARC) NIST SP 800-45, “Guidelines on Electronic Mail Security”
Question 15:
A security administrator needs to automate alerting. The server generates structured log files that need to be parsed to determine whether an alarm has been triggered Given the following code function:
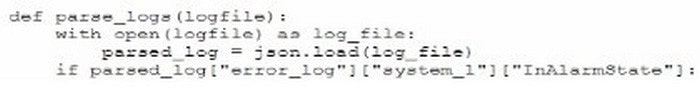
Which of the following is most likely the log input that the code will parse?
A. [“error_log] [“system_1”] [“InAlarmState”: True]
B. <“error_log”><“system_1”>
C. error_log;
-system_1:
InAlarmState: True
D. {“error_log”: {“system_1”: {“InAlarmState”: True}}}
Correct Answer: A
The code function provided in the question seems to be designed to parse JSON formatted logs to check for an alarm state. Option A is a JSON format that matches the structure likely expected by the code. The presence of the “error_log”
and “InAlarmState” keys suggests that this is the correct input format.
Reference: CompTIA SecurityX Study Guide, Chapter on Log Management and Automation, Section on Parsing Structured Logs.
These practice questions are just a warm-up and aren’t enough to truly pass the CompTIA SecurityX (formerly CASP+) CAS-005 certification exam.
A more comprehensive collection of CompTIA CAS-005 study resources
To make it easier for you to learn, each resource comes with a link that you can access directly.
Video Format
- CompTIA CertMaster Learn + Labs: https://www.comptia.org/training/certmaster-learn
- CompTIA Official Channel: https://www.youtube.com/@CompTIATV
- Professor Messer’s CASP+ Study Group: https://www.youtube.com/@professormesser
- Cybersecurity Training by Edureka: https://www.youtube.com/@edurekaIN
Book Format
- CompTIA SecurityX CAS-005 Official Study Guide: https://store.comptia.org/products/the-official-comptia-casp-self-paced-study-guide-exam-cas-004[](https://store.comptia.org/the-official-comptia-casp-self-paced-study-guide-exam-cas-004-ebook/p/CAS-004-SPDB-21-C)
- CASP+ CompTIA Advanced Security Practitioner Study Guide: Exam CAS-004 (Sybex): https://www.amazon.com/CASP-CompTIA-Advanced-Security-Practitioner/dp/1119813123[](https://www.amazon.com/CASP-Advanced-Practitioner-Authorized-Courseware/dp/1118083199)
- CompTIA Advanced Security Practitioner (CASP) CAS-003 Cert Guide: https://www.amazon.com/CompTIA-Advanced-Security-Practitioner-Certification/dp/0789759446[](https://www.amazon.com/CompTIA-Advanced-Security-Practitioner-Certification/dp/0789759446)
Document Format
- CompTIA CAS-005 Exam Objectives: https://www.comptia.org/certifications/casp#examdetails
- Free CASP+ Study Notes (1000+ pages PDF): https://www.howtonetwork.com/courses/comptia/comptia-casp-certification/[](https://www.reddit.com/r/CompTIA/comments/xczkja/comptia_casp_study_guide_free_download_1005_pages/)
Practicing for the exam by using CAS-005 dumps and study resources is the smartest choice.
Top Questions About the Exam, Certification, and Career
Who is the CompTIA SecurityX (CAS-005) certification suitable for?
It’s suitable for professionals with at least 10 years of IT experience (including 5 years in cybersecurity), such as security architects, senior security engineers, or technical leads.
What is the structure and format of the CAS-005 exam?
The exam includes up to 90 questions, comprising multiple-choice and performance-based questions (PBQs), with a duration of 165 minutes and a dynamic passing score (no fixed
How does the CAS-005 certification help with career opportunities?
CAS-005 validates advanced security architecture and engineering skills, ideal for senior roles like security architect or CISO, with average salaries of $120,000-$150,000/year (U.S. market).
How long is the CAS-005 certification valid, and how can it be renewed?
The certification is valid for 3 years. It can be renewed by earning 60 Continuing Education Units (CEUs) through CompTIA’s Continuing Education (CE) program or by obtaining a higher-level certification.
Finally I want to say
To prepare for the CompTIA CAS-005 certification exam, the latest free CAS-005 dumps with practice questions have been shared with you. All you need to do is take action.
More importantly, get the latest CAS-005 dumps at https://www.leads4pass.com/cas-005.html, available in both PDF and VCE practice modes for you to choose from.
Remember, passing the CompTIA CAS-005 certification exam will bring you significant benefits, including better job opportunities, salary growth, and increased competitiveness.





