leads4pass SY0-601 Dumps contains 1093 latest exam questions and answers, covering more than 90% of CompTIA SY0-601 “CompTIA Security+ 2023” actual exam questions! For your best Exam Solutions.
leads4pass SY0-601 exam questions and answers are updated throughout the year! Guaranteed to be available anytime! Download SY0-601 Dumps: https://www.leads4pass.com/sy0-601.html
One-time use 365 days free update! You can also choose the learning method that suits you according to your learning habits: PDF and VCE learning formats are provided to help you learn easily and pass CompTIA SY0-601 Security+ Exam successfully.
Here you can always get more: leads4pass SY0-601 dumps page provides download free Demo for you to experience, you can also participate in the following online practice tests
Latest CompTIA SY0-601 dumps Exam Questions
| From | Number of exam questions | Associated certification | Online Download | Last update |
| leads4pass | 13 | CompTIA Security+ | SY0-601 PDF | SY0-601 Dumps |
NEW QUESTION 1:
Which of the following BEST describes the team that acts as a referee during a penetration-testing exercise?
A. White team
B. Purple team
C. Green team
D. Blue team
E. Red team
Correct Answer: D
NEW QUESTION 2:
A security administrator Is managing administrative access to sensitive systems with the following requirements:
Common login accounts must not be used (or administrative duties.
Administrative accounts must be temporal in nature.
Each administrative account must be assigned to one specific user.
Accounts must have complex passwords.
Audit trails and logging must be enabled on all systems.
Which of the following solutions should the administrator deploy to meet these requirements?
A. ABAC
B. SAML
C. PAM
D. CASB
Correct Answer: C
Explanation: The best solution to meet the given requirements is to deploy a Privileged Access Management (PAM) solution.
PAM solutions allow administrators to create and manage administrative accounts that are assigned to specific users and that have complex passwords. Additionally, PAM solutions provide the ability to enable audit trails and logging on all systems, as well as to set up temporal access for administrative accounts.
SAML, ABAC, and CASB are not suitable for this purpose.
NEW QUESTION 3:
A security administrator is trying to determine whether a server is vulnerable to a range of attacks. After using a tool, the administrator obtains the following output:
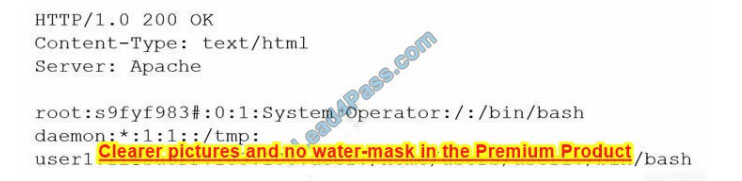
Which of the following attacks was successfully implemented based on the output?
A. Memory leak
B. Race conditions
C. SQL injection
D. Directory traversal
Correct Answer: D
A – Memory Leak – If there was a memory leak, the first line of the HTTP header probably wouldn’t be HTTP/1.0 200 OK because it\’d likely result in the server crashing. It is possible to have an ongoing memory leak without crashing the server, but there is no evidence of that.
B – Race conditions – There is no evidence of race conditions.
C – SQL injection – There is no evidence of SQL injection.
D – Directory Traversal – This picture shows the output of an HTTP response, including both a header (first three lines) and a body. An HTTP response should not contain a body, especially one consisting of the contents of the password file.
So the HTTP request was probably something like “example.com/../../../../../../../etc/passwd”.
NEW QUESTION 4:
A user\’s laptop constantly disconnects from the Wi-Fi network. Once the laptop reconnects, the user can reach the internet but cannot access shared folders or other network resources.
Which of the following types of attacks is the user MOST likely experiencing?
A. Bluejacking
B. Jamming
C. Rogue access point
D. Evil twin
Correct Answer: D
Explanation: An evil twin attack is when an attacker sets up a fake Wi-Fi network that looks like a legitimate network but is designed to capture user data that is sent over the network.
In this case, the user\’s laptop is constantly disconnecting and reconnecting to the Wi-Fi network, indicating that it is connecting to the fake network instead of the legitimate one.
Once the user connects to the fake network, they are unable to access shared folders or other network resources, as those are only available on the legitimate network.
NEW QUESTION 5:
Which of the following incident response steps occurs before containment?
A. Eradication
B. Recovery
C. Lessons learned
D. Identification
Correct Answer: D
NEW QUESTION 6:
A security analyst is designing the appropriate controls to limit unauthorized access to a physical site. The analyst has a directive to utilize the lowest possible budget.
Which of the following would BEST meet the requirements?
A. Preventive controls
B. Compensating controls
C. Deterrent controls
D. Detective controls
Correct Answer: C
Deterrent makes sense on further thought. The question just states unauthorized access. It doesn’t state the intent of any unauthorized intruders.
Deterrence is designed to reduce the occurrence of unintentional bystanders or unmotivated malicious agents entering the site. Should the agent be motivated enough, a preventative measure is needed. But
again, the question doesn’t list intentions.
Therefore this method works to limit the number of unauthorized visitors by weeding out everyone but the motivated, and the truly stupid.
NEW QUESTION 7:
Digital signatures use asymmetric encryption. This means the message is encrypted with:
A. the sender\’s private key and decrypted with the sender\’s public key
B. the sender\’s public key and decrypted with the sender\’s private key
C. the sender\’s private key and decrypted with the recipient\’s public key.
D. the sender\’s public key and decrypted with the recipient\’s private key
Correct Answer: A
There are 2 general ways to use asymmetric algorithms.
1 – For communication between 2 hosts: If Bob sends a message to Alice, Bob uses Alice\’s public key to encrypt the message, and Alice uses her private key to decrypt the message.
2 – For digital signature/Authentication: If Alice needs to authenticate Bob, BOB uses his private key to sign the message, and Alice uses the public key of Bob to decrypt the message.
This process helps to make sure the signature is owned by Bob. In this example, A is totally correct.
NEW QUESTION 8:
A security analyst needs to implement an MDM solution for BYOD users that will allow the company to retain control over company emails residing on the devices and limit data exfiltration that might occur if the devices are lost or stolen.
Which of the following would BEST meet these requirements? (Select TWO).
A. Full-device encryption
B. Network usage rules
C. Geofencing
D. Containerization
E. Application whitelisting
F. Remote control
Correct Answer: AB
NEW QUESTION 9:
Which of the following controls would provide the BEST protection against tailgating?
A. Access control vestibule
B. Closed-circuit television
C. Proximity card reader
D. Faraday cage
Correct Answer: A
NEW QUESTION 10:
A user enters a username and a password at the login screen for a web portal. A few seconds later the following message appears on the screen: Please use a combination of numbers, special characters, and letters in the password field.
Which of the following concepts does this message describe?
A. Password complexity
B. Password reuse
C. Password History
D. Password age
Correct Answer: A
Password complexity – is the method that obligates users to use passwords this some characteristics.
NEW QUESTION 11:
Which of the following is the MOST effective control against zero-day vulnerabilities?
A. Network segmentation
B. Patch management
C. Intrusion prevention system
D. Multiple vulnerability scanners
Correct Answer: A
IPS can only protect against known host and application-based attacks and exploits. IPS inspects traffic against signatures and anomalies, it does cover a broad spectrum of attack types, most of them signature-based, and signatures alone cannot protect against zero-day attacks. (www.rawcode7.medium.com)
However, with network segmentation, you\’re able to isolate critical assets into different segments. And when a zero-day attack occurs, you\’re not at risk of losing all and are able to isolate the attack\’s effect to one segment.
NEW QUESTION 12:
A technician enables full disk encryption on a laptop that will be taken on a business trip. Which of the following does this process BEST protect?
A. Data in transit
B. Data in processing
C. Data at rest
D. Data tokenization
Correct Answer: C
Data at rest: Data at rest is data in its stored or resting state, which is typically on some type of persistent storage such as a hard drive or tape. Symmetric encryption is used in this case.
NEW QUESTION 13:
Which of the following would be used to find the MOST common web application vulnerabilities?
A. OWASP
B. MITRE ATTandCK
C. Cyber Kill Chain
D. SDLC
Correct Answer: A
Anything related to WEB APPLICATION SECURITY = OWASP The Open Web Application Security Project
(FRAMEWORK) is an online community that produces freely-available articles, methodologies, documentation, tools, and technologies in the field of web application security.
The Open Web Application Security Project provides free and open resources. MITRE\’s Adversarial Tactics, Techniques, and Common Knowledge (ATTandCKTM) is a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary\’s lifecycle and the platforms they are known to target.
ATTandCK is useful for understanding security risks against known adversary behavior, for planning security improvements, and verifying defenses work as expected.
…
leads4pass SY0-601 Dumps contains 1093 latest exam questions and answers, one-time use enjoys free updates for 365 days! It also provides PDF and VCE multiple learning formats to assist you in easily learning and passing the CompTIA SY0-601 Security+ Exam!
Use CompTIA SY0-601 Security+ Exam Solutions: Download SY0-601 dumps with PDF and VCE: https://www.leads4pass.com/sy0-601.html, to help you pass the exam 100% successfully.