The CompTIA SY0-601 exam is a very specific exam item, the 2022 listed exam item, CompTIA SY0-601 exam: “CompTIA Security+ 2022”. Passing the CompTIA SY0-601 exam can help you enter the field. Actual valid CompTIA SY0-601 dumps updated throughout the year to PDF and VCE in Lead4Pass: https://www.leads4pass.com/sy0-601.html (PDF + VCE) to help you successfully pass your first exam. You can also take our free shared online exam.
Check out the CompTIA sy0-601 PDF available free of charge in 2022:
https://drive.google.com/file/d/1-3cH41u_Mx_ZGHfP6rRjkzrk0lexWpY_/
https://drive.google.com/file/d/15yTMzIypZ64KRobr5X7Bu9fuOx5oneHL/
https://drive.google.com/file/d/1lJ911sJMs1cOPYD3MCKznr89c5s5KTn5/
https://drive.google.com/file/d/1_ij2vKQ_V5lWRMAfyPhC_vzDXyIPfzHI/
Check out the CompTIA sy0-601 dumps exam questions and answers available in the new release:
New Question 1:
SIMULATION
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
1.
Deny cleartext web traffic.
2.
Ensure secure management protocols are used.
3.
Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
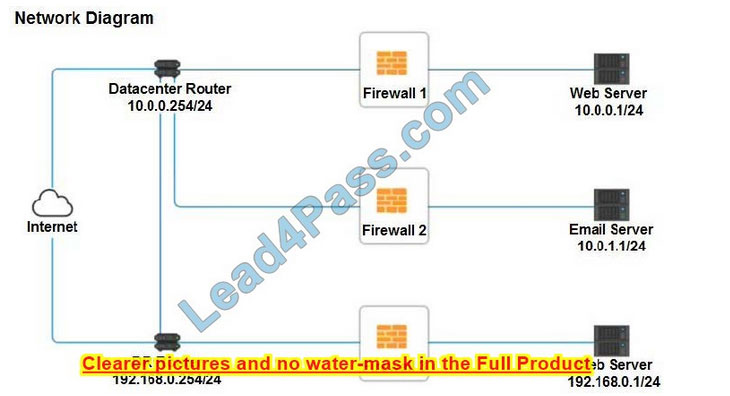
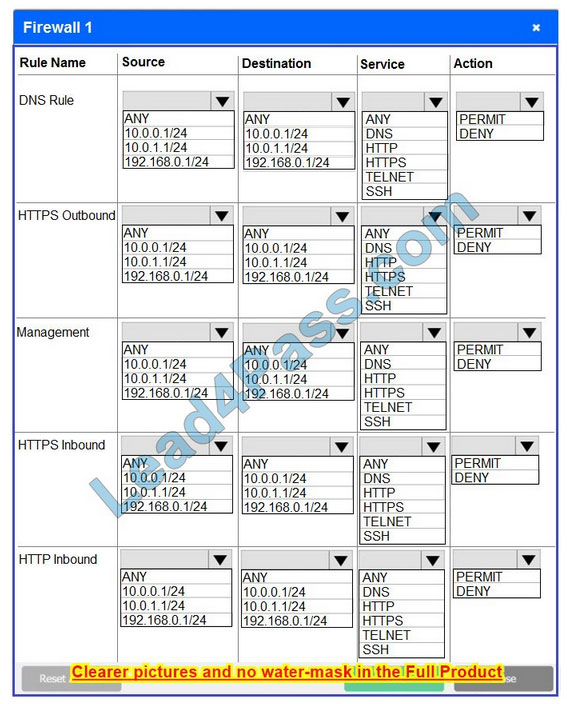
Firewall 1 Hot Area:
Correct Answer:
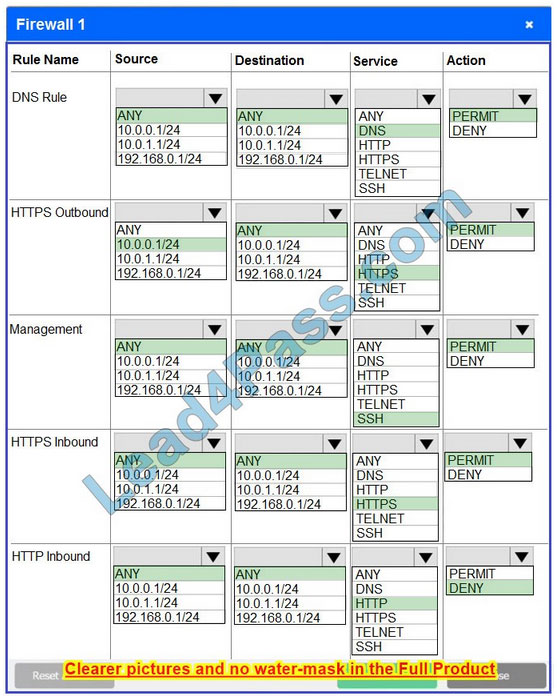
In Firewall 1, HTTP inbound Action should be DENY. As shown below
Firewall 1: DNS Rule: ANY ->; ANY ->; DNS ->; PERMIT HTTPS Outbound: 10.0.0.1/24 ->; ANY ->; HTTPS ->; PERMIT Management: ANY ->; ANY ->; SSH ->; PERMIT HTTPS Inbound: ANY ->; ANY ->; HTTPS ->; PERMIT HTTP Inbound: ANY ->; ANY ->; HTTP ->; DENY
New Question 2:
SIMULATION
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
1.
Deny cleartext web traffic.
2.
Ensure secure management protocols are used.
3.
Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
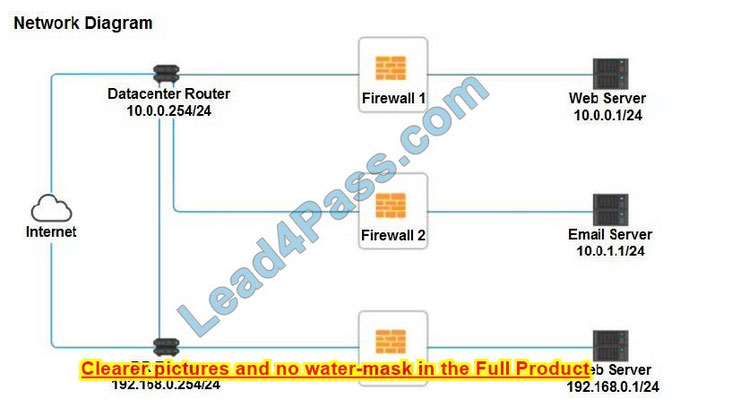
Firewall 2
Hot Area:
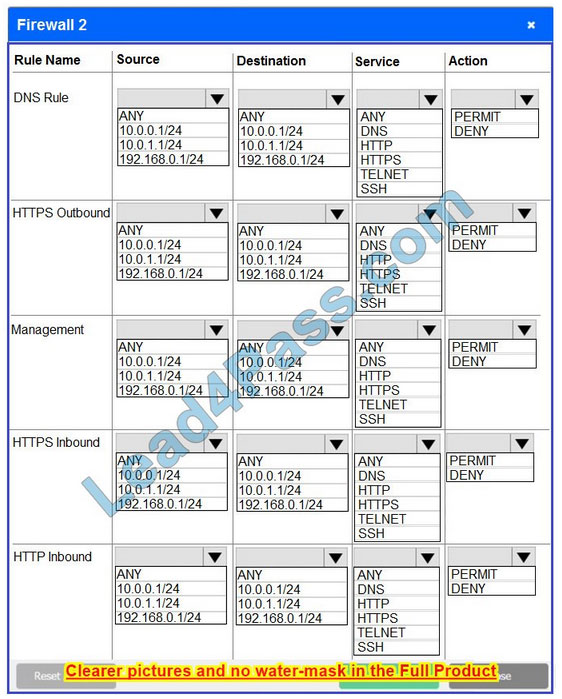
Correct Answer:
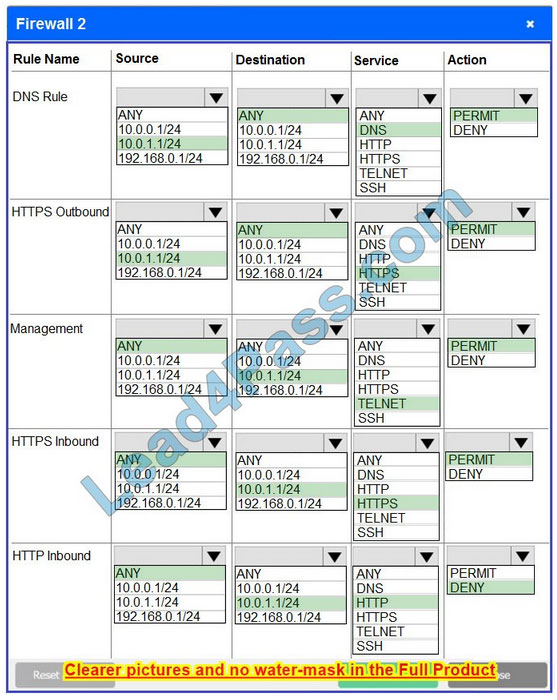
Firewall 2: No changes should be made to this firewall
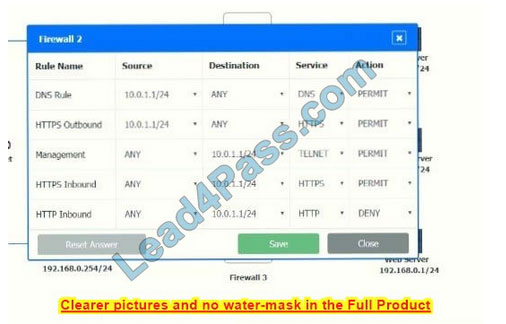
New Question 3:
SIMULATION
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
1.
Deny cleartext web traffic.
2.
Ensure secure management protocols are used.
3.
Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
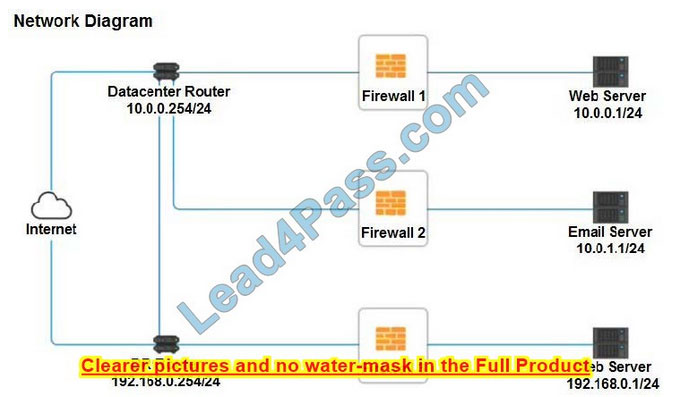
Firewall 3 Hot Area:
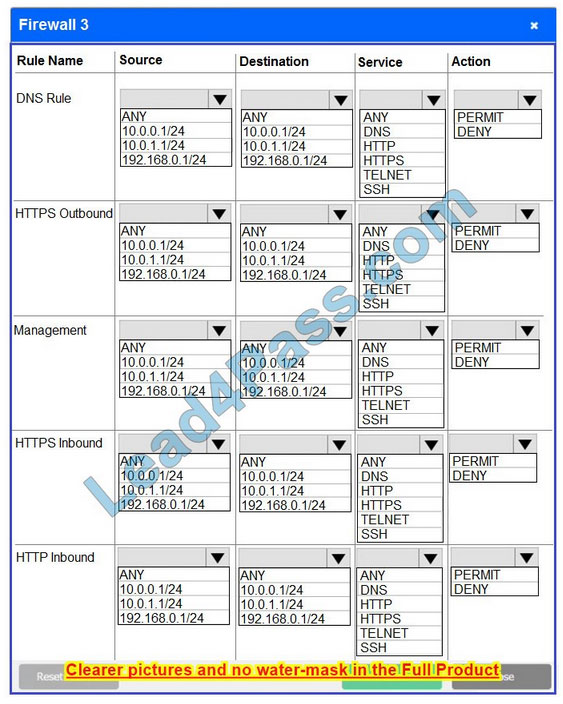
Correct Answer:
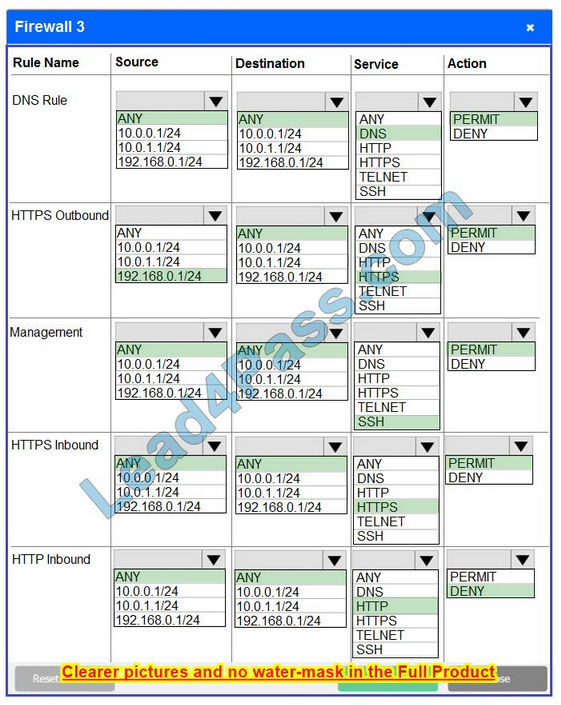
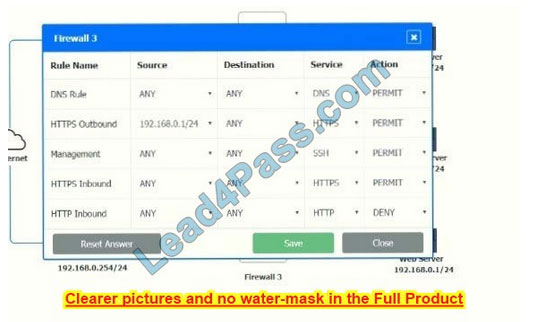
Firewall 3:
DNS Rule: ANY ->; ANY ->; DNS ->; PERMIT HTTPS Outbound: 192.168.0.1/24 ->; ANY ->; HTTPS ->; PERMIT Management: ANY ->; ANY ->; SSH ->; PERMIT HTTPS Inbound: ANY ->; ANY ->; HTTPS ->; PERMIT HTTP Inbound: ANY ->; ANY ->; HTTP ->; DENY
New Question 4:
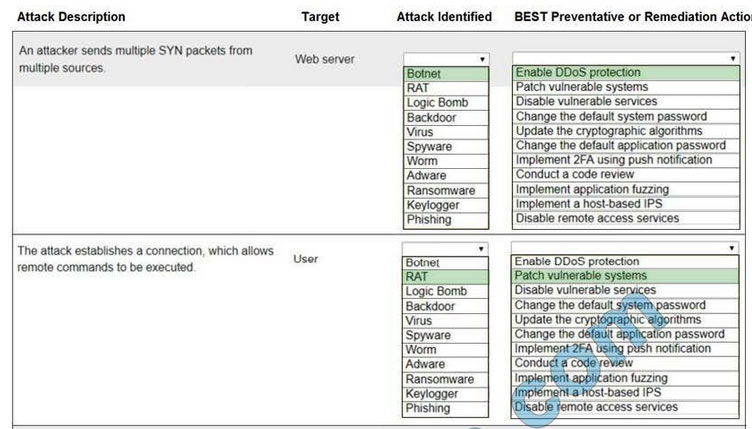
HOTSPOT
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Hot Area:
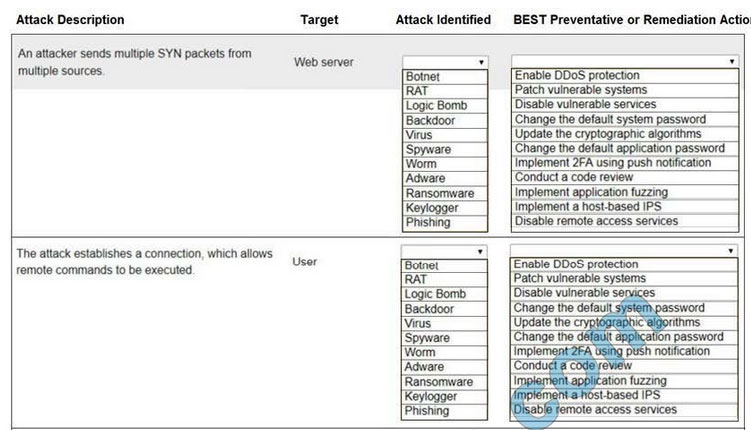
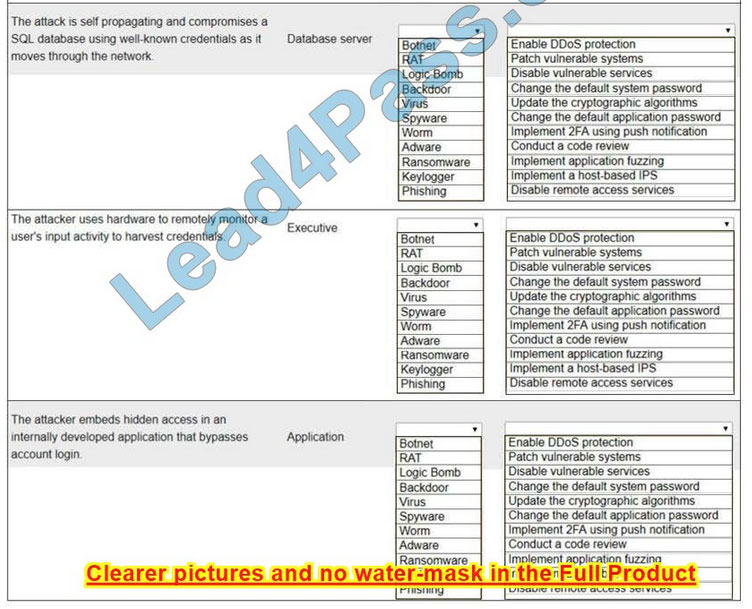
Correct Answer:
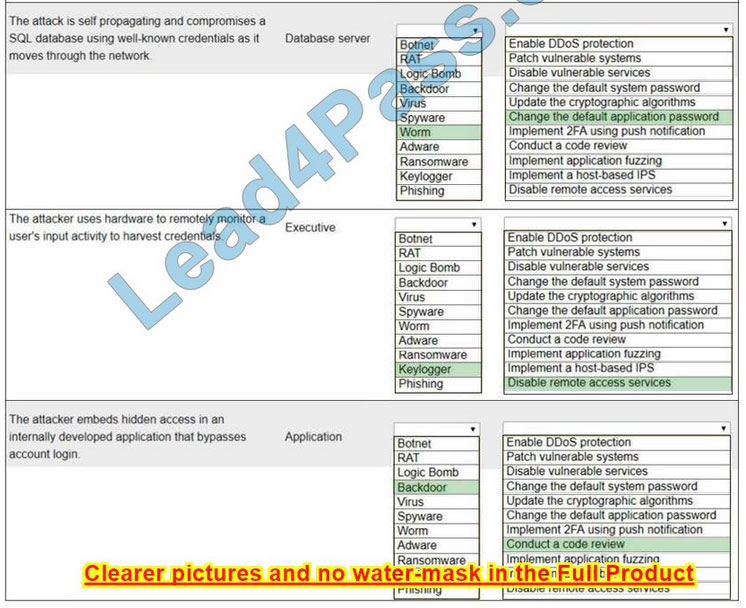
New Question 5:
HOTSPOT
Select the appropriate attack from each drop-down list to label the corresponding illustrated attack Instructions: Attacks may only be used once and will disappear from the drop-down list if selected. When you have completed the simulation, please select the Done button to submit.
Hot Area:
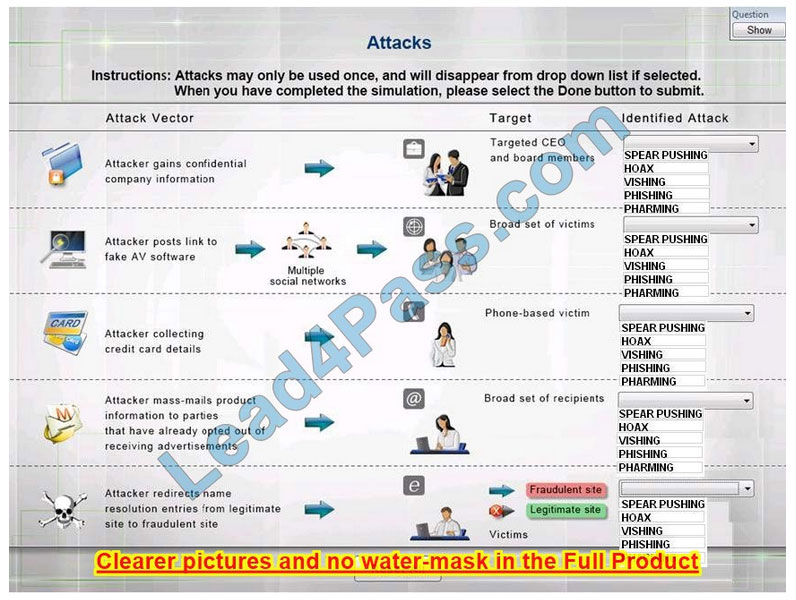
Correct Answer:
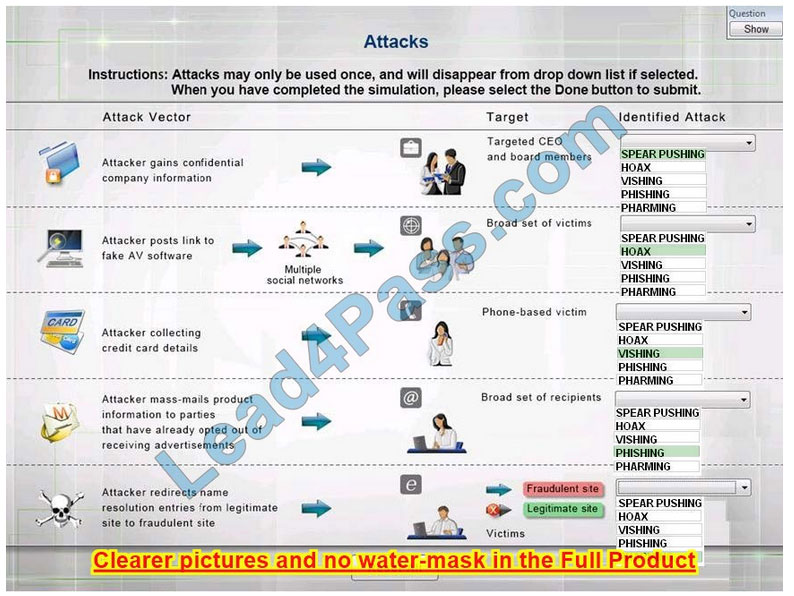
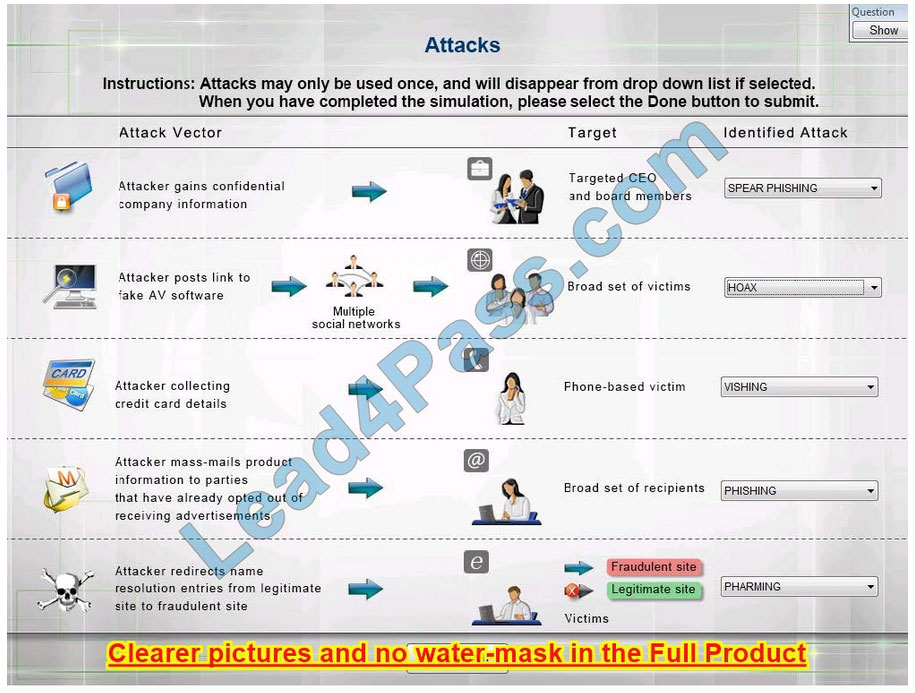
1: Spear phishing is an e-mail spoofing fraud attempt that targets a specific organization,seeking unauthorized access to confidential data.
As with the e-mail messages used in regular phishing expeditions, spear phishing messages appear to come from a trusted source.
Phishing messages usually appear to come from a large and well-known company or Web site with a broad membership base, such as eBay or PayPal.
In the case of spear phishing, however, the apparent source of the e-mail is likely to be an individual within the recipient\’s own company and generally someone in a position of authority.
2: The Hoax in this question is designed to make people believe that the fake AV (antivirus) software is genuine.
3: Vishing is the act of using the telephone in an attempt to scam the user into surrendering private information that will be used for identity theft.
The scammer usually pretends to be a legitimate business, and fools the victim into thinking he or she will profit.
4: Phishing is the act of sending an email to a user falsely claiming to be an established legitimate enterprise in an attempt to scam the user into surrendering private information that will be used for identity theft.
Phishing emails will direct the user to visit a website where they are asked to update personal information, such as a password, credit card, social security, or bank account numbers, that the legitimate organization already has.
The website, however, is bogus and set up only to steal the information the user enters on the page.
5: Similar in nature to e-mail phishing, pharming seeks to obtain personal or private (usually financial related) information through domain spoofing.
Rather than being spammed with malicious and mischievous e-mail requests for you to visit spoof Web sites that appear legitimate, pharming \’poisons\’ a DNS server by infusing false information into the DNS server, resulting in a user\’s request being redirected elsewhere.
Your browser, however, will show you are at the correct
Web site, which makes pharming a bit more serious and more difficult to detect. Phishing attempts to scam people one at a time with an e-mail while pharming allows the scammers to target large groups of people at one time through domain spoofing.
New Question 6:
HOTSPOT
The security administrator has installed a new firewall that implements an implicit DENY policy by default. Click on the firewall and configure it to allow ONLY the following communication.
1.
The Accounting workstation can ONLY access the web server on the public network over the default HTTPS port. The accounting workstation should not access other networks.
2.
The HR workstation should be restricted to communicating with the Financial server ONLY, over the default SCP port
3.
The Admin workstation should ONLY be able to access the servers on the secure network over the default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first match The port number must be typed in and only one port number can be entered per rule Type ANY for all ports. The original firewall configuration can
be reset at any time by pressing the reset button. Once you have met the simulation requirements, click save and then Done to submit.
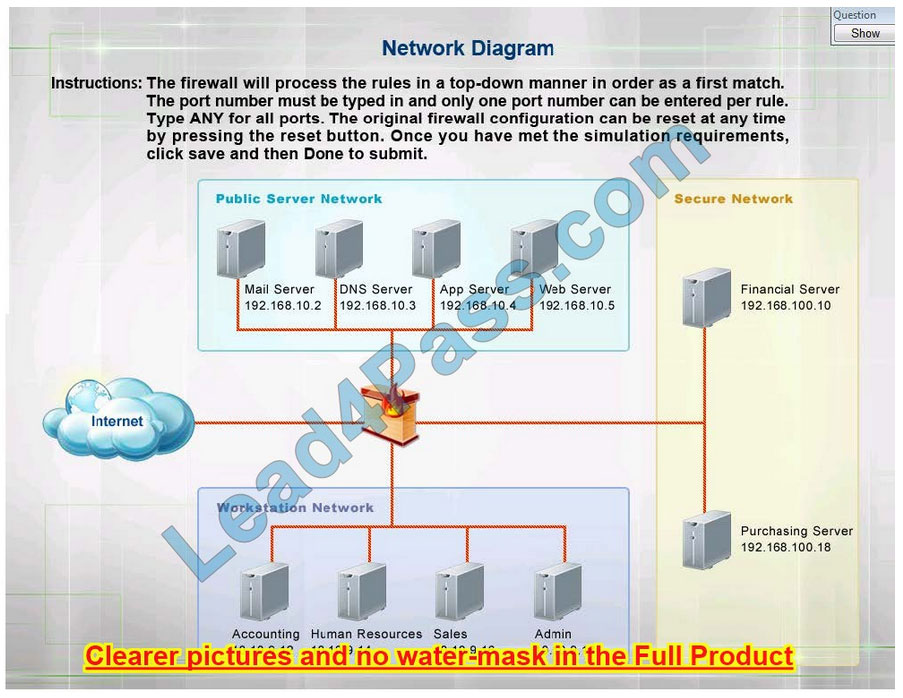
Hot Area:
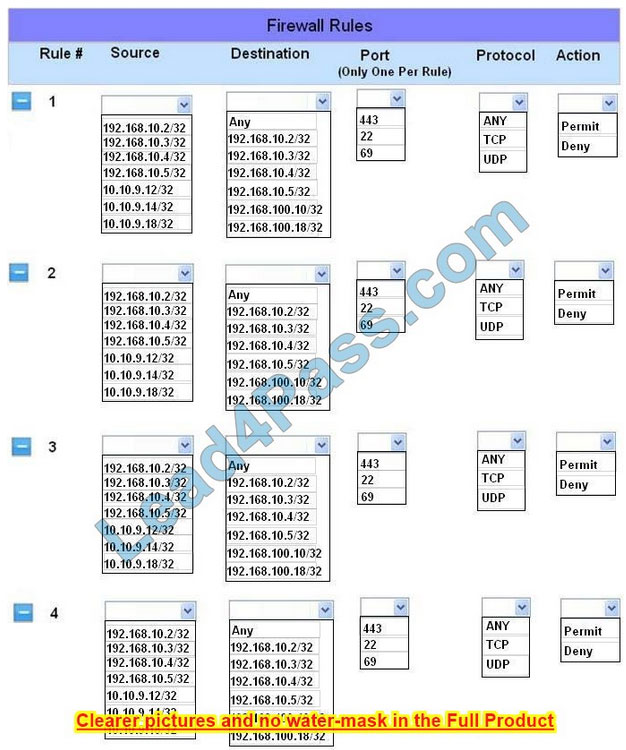
Correct Answer:
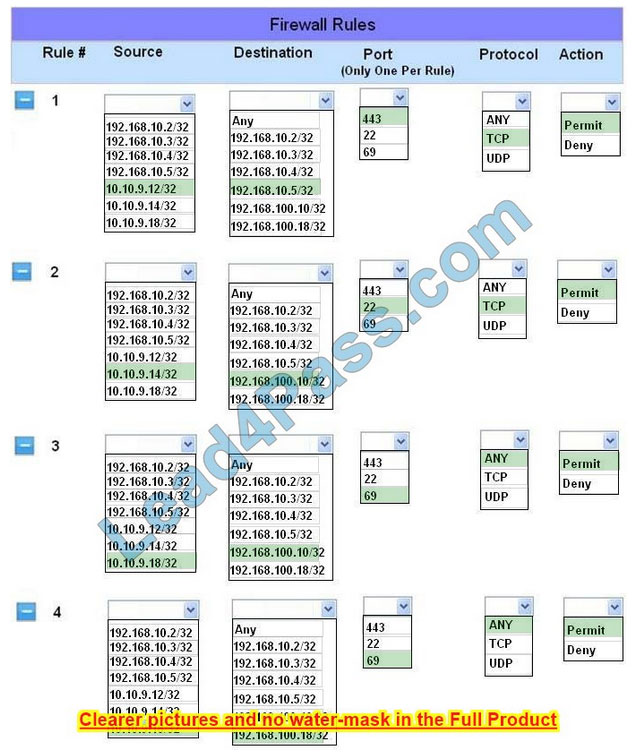
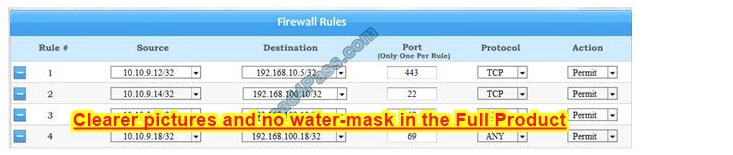
Implicit deny is the default security stance that says if you aren\’t specifically granted access or privileges for a resource, you’re denied access by default.
Rule #1 allows the Accounting workstation to ONLY access the web server on the public network over the default HTTPS port, which is TCP port 443.
Rule #2 allows the HR workstation to ONLY communicate with the Financial server over the default SCP port, which is TCP Port 22
Rule #3 and Rule #4 allow the Admin workstation to ONLY access the Financial and Purchasing servers located on the secure network over the default TFTP port, which is Port 69.
References:
Stewart, James Michael, CompTIA Security+ Review Guide, Sybex, Indianapolis, 2014, pp.26, 44
New Question 7:
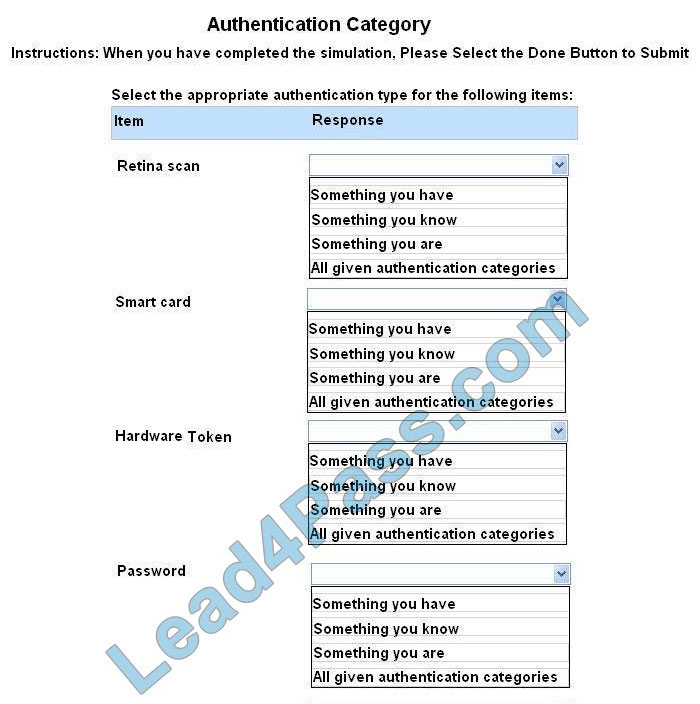

Correct Answer:
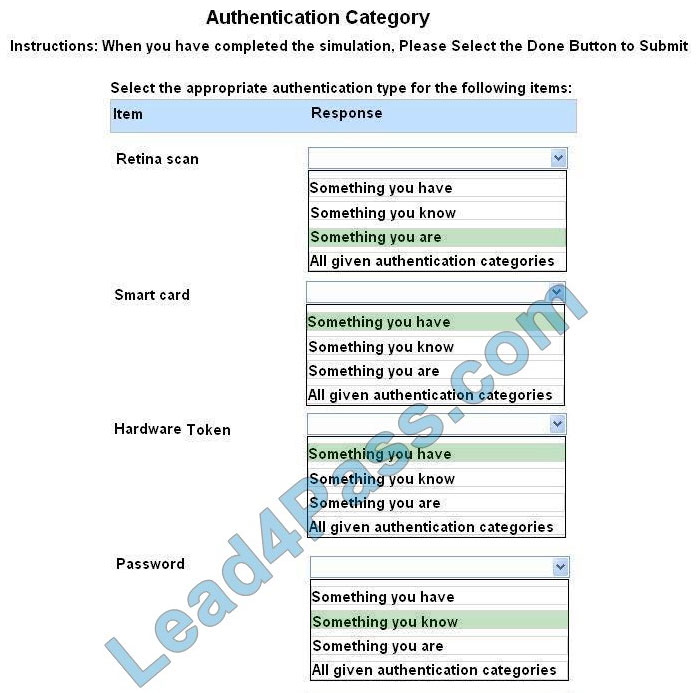

Something you are includes fingerprints, retina scans, or voice recognition.
Something you have includes smart cards, token devices, or keys.
Something you know includes passwords, codes, PINs, combinations, or secret phrases.
Somewhere you are including a physical location s or logical addresses, such as a domain name, an IP address, or a MAC address.
Something you do includes your typing rhythm, a secret handshake, or a private knock.
References:
Stewart, James Michael, CompTIA Security+ Review Guide, Sybex, Indianapolis, 2014, p. 285
New Question 8:
HOTSPOT
For each of the given items, select the appropriate authentication category from the drop down choices. Select the appropriate authentication type for the following items:
Hot Area:
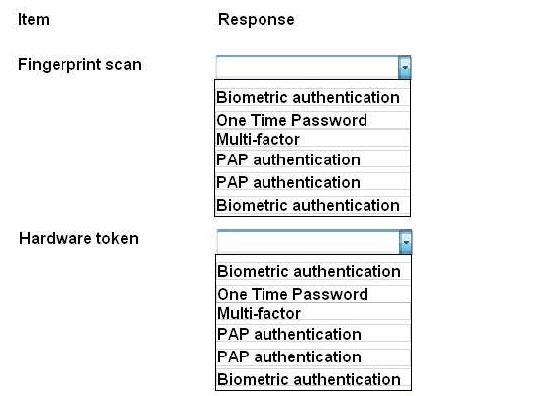
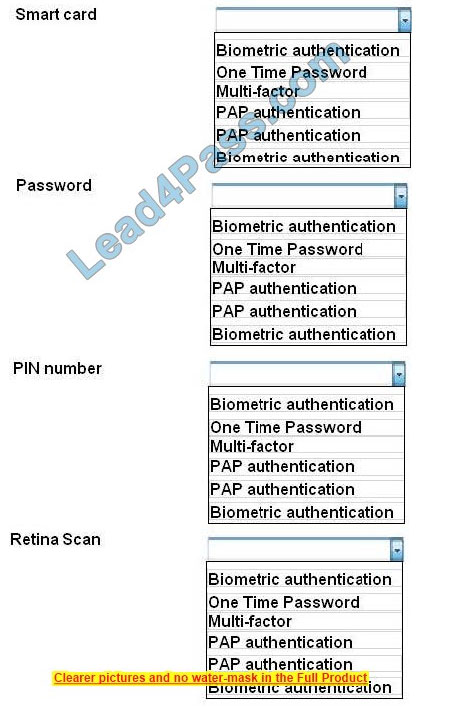
Correct Answer:
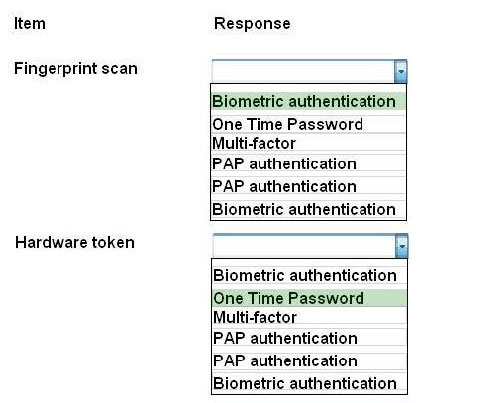
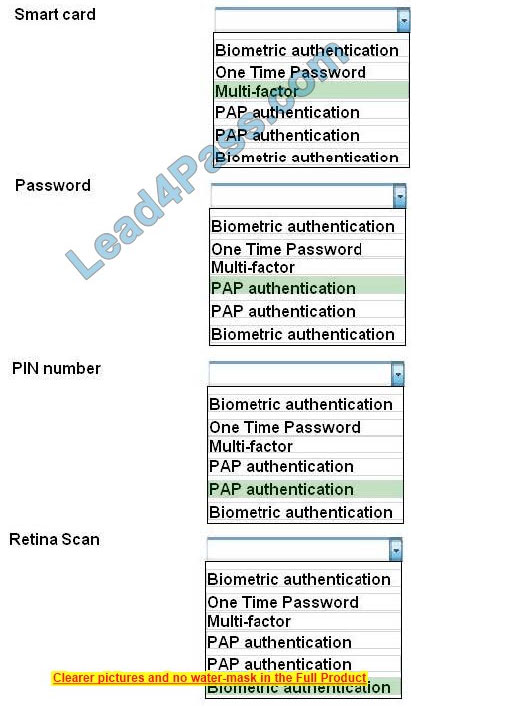
Biometrics refers to a collection of physical attributes of the human body that can be used as identification or an authentication factor. Fingerprints and retinas are physical attributes of the human body.
Two types of tokens exist, Time-based one-time password (TOTP) tokens and HMACbased one-time password (HOTP). TOTP tokens generate passwords at fixed time intervals, whereas HOTP tokens generate passwords not based on fixed
time intervals but instead based on a non-repeating one-way function, such as a hash or HMAC operation.
Smart cards can have Multi-factor and proximity authentication embedded into it.
PAP allows for two entities to share a password in advance and use the password as the basis of authentication. The same goes for PIN numbers.
New Question 9:
HOTSPOT
A newly purchased corporate WAP needs to be configured in the MOST secure manner possible.
INSTRUCTIONS
Please click on the below items on the network diagram and configure them accordingly:
1.
WAP
2.
DHCP Server
3.
AAA Server
4.
Wireless Controller
5.
LDAP Server
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
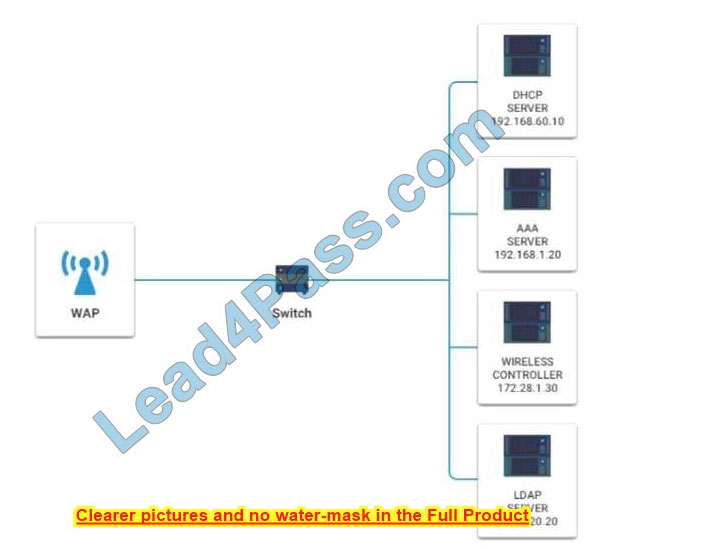
Hot Area:
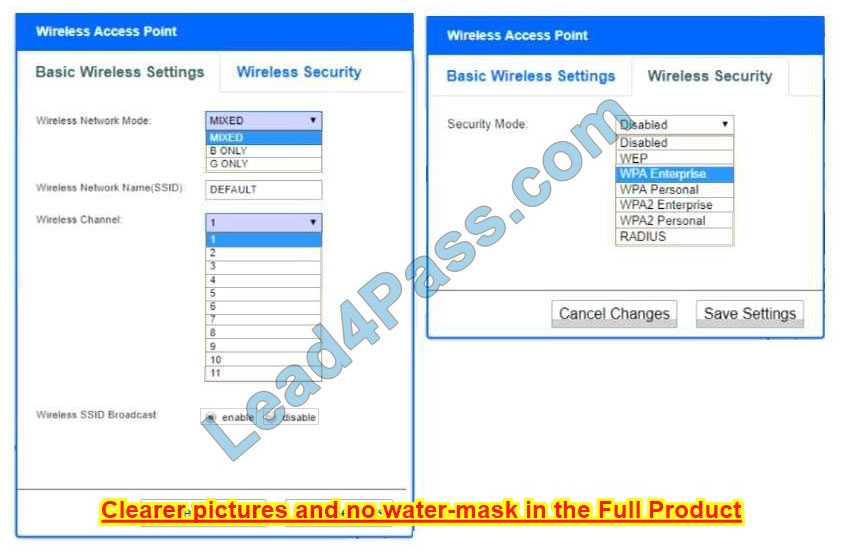
Correct Answer:
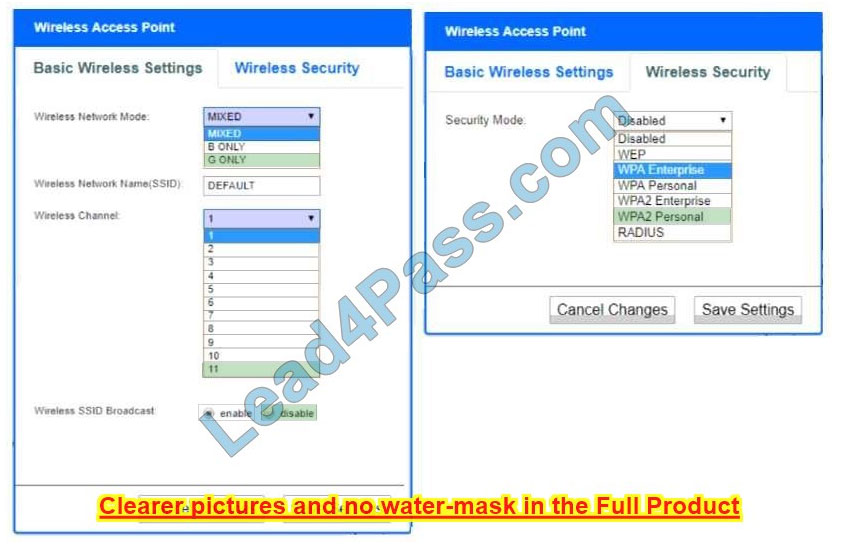
Wireless Access Point:
1.
Network Mode – G only
2.
Wireless Channel – 11
3.
Wireless SSID Broadcast – disable
4.
Security settings – WPA2 Personal
New Question 10:
DRAG DROP
A security auditor is reviewing the following output from file integrity monitoring software installed on a very busy server at a large service provider. The server has not been updates since it was installed. Drag and drop the log entry that identifies the first instance of server compromise.
Hot Area:
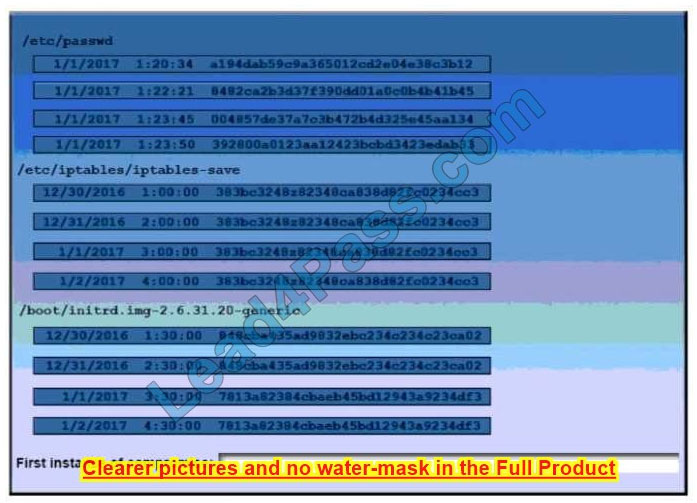
Correct Answer:

New Question 11:
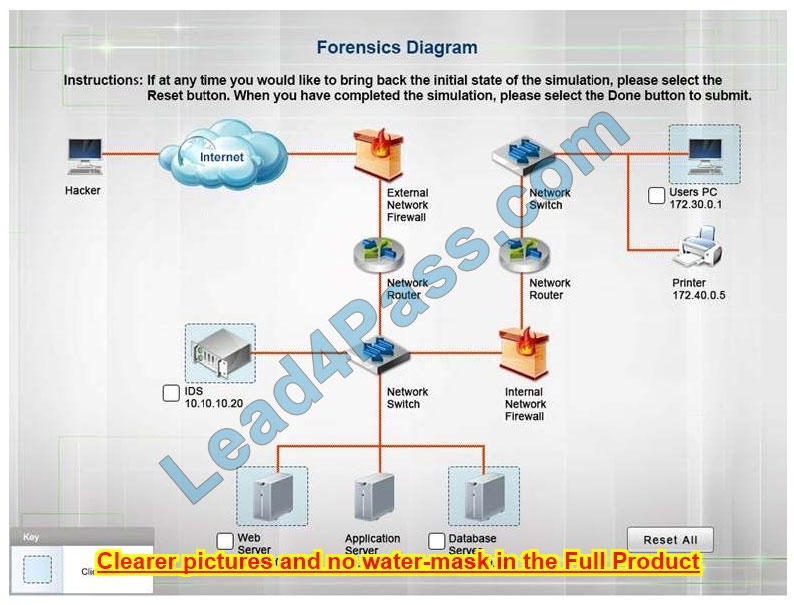
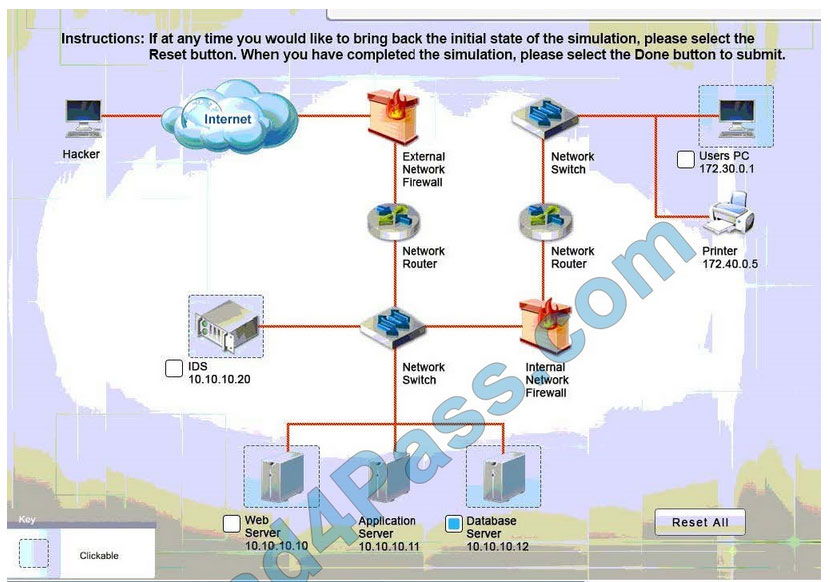
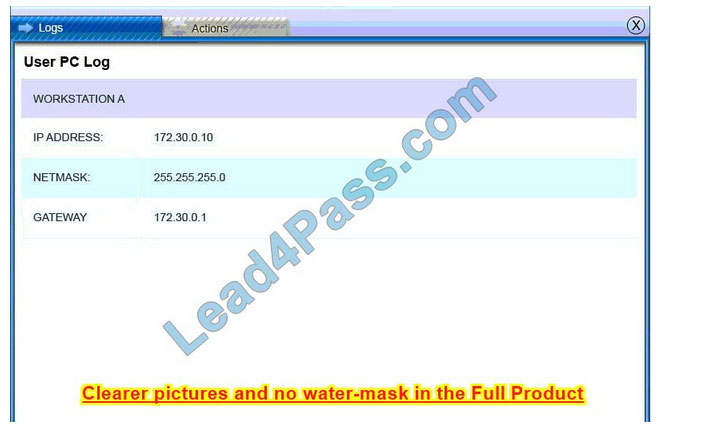
A security administrator discovers that an attack has been completed against a node on the corporate network. All available logs were collected and stored.
You must review all network logs to discover the scope of the attack, check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. The environment is
a critical production environment; perform the LEAST disruptive actions on the network, while still performing the appropriate incident responses.
Instructions: The web server, database server, IDS, and User PC are clickable. Check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. Not all
actions may be used, and order is not important. If at anytime you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit.
Once the simulation is submitted, please select the Next button to continue.
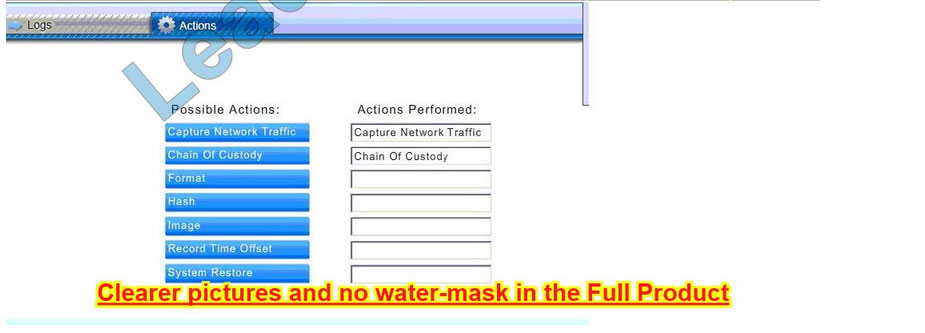
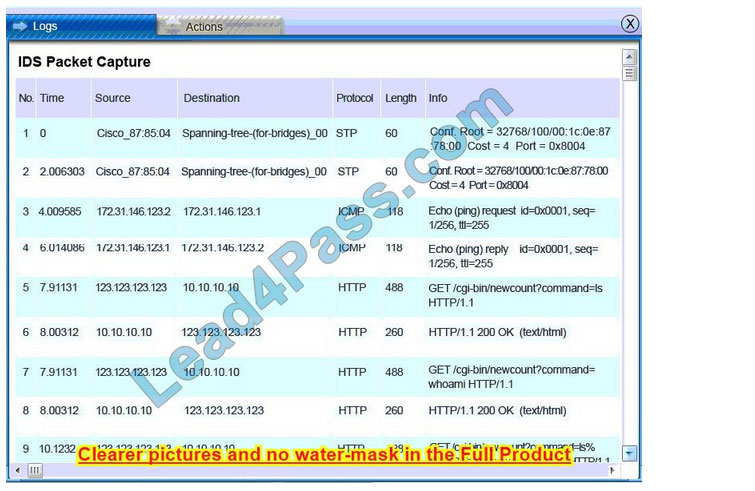
Database server was attacked; actions should be to capture network traffic and Chain of Custody.
(The database server logs shows the Audit Failure and Audit Success attempts)It is only logical that all the logs will be stored on the database server and the least disruption action on the network to take as a response to the incident would be
to check the logs (since these are already collected and stored) and maintain a chain of custody of those logs.
Correct Answer:
IDS Server Log:
Web Server Log: Database Server Log:
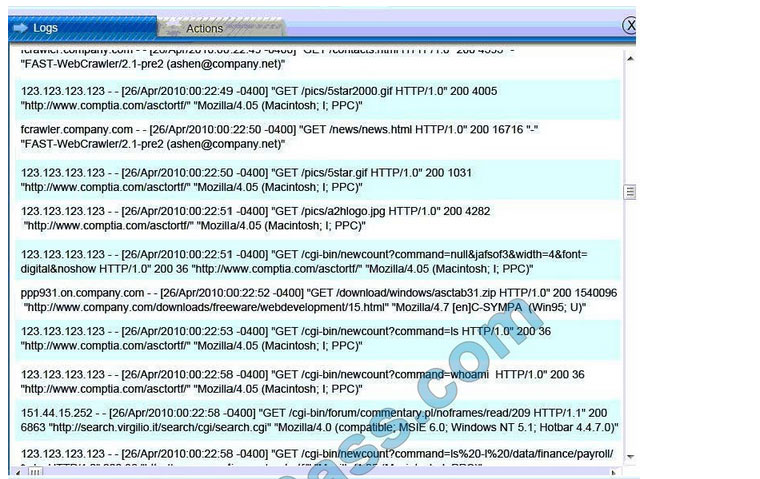
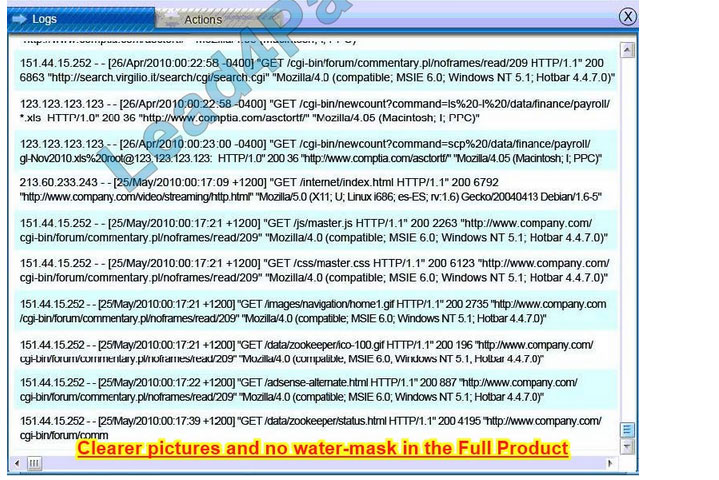
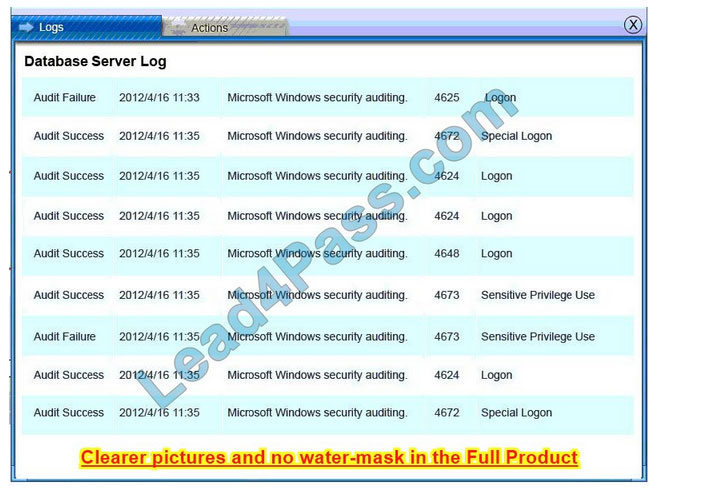
Users PC Log:
New Question 12:
Task: Configure the firewall (fill out the table) to allow these four rules:
Only allow the Accounting computer to have HTTPS access to the Administrative server.
Only allow the HR computer to be able to communicate with the Server 2 System over SCP.
Allow the IT computer to have access to both Administrative Server 1 and Administrative Server 2
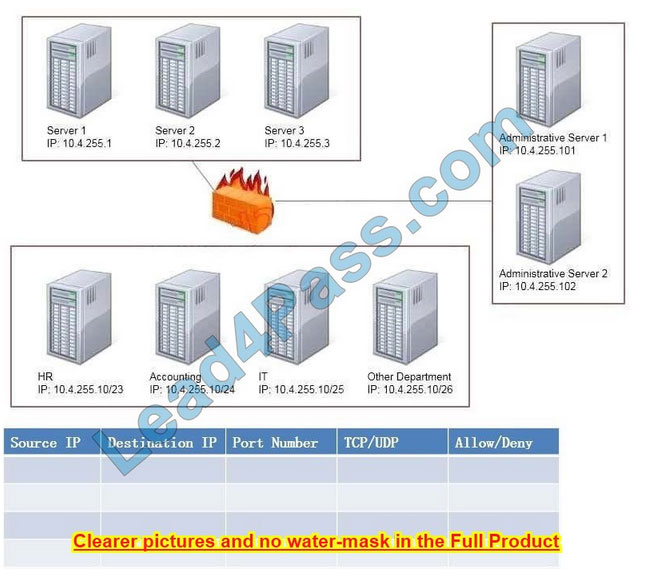
Correct Answer:
Use the following answer for this simulation task.
Below table has all the answers required for this question.

Firewall rules act like ACLs, and they are used to dictate what traffic can pass between the firewall and the internal network. Three possible actions can be taken based on the rule\’s criteria: Block the connection Allow the connection Allow the connection only if it is secured TCP is responsible for providing a reliable, one-to-one, connection-oriented session. TCP establishes a connection and ensures that the other end receives any packets sent. Two hosts communicate packet results with each other. TCP also ensures that packets are decoded and sequenced properly. This connection is persistent during the session. When the session ends, the connection is torn down. UDP provides an unreliable connectionless communication method between hosts. UDP is considered a best-effort protocol, but it\’s considerably faster than TCP. The sessions don\’t establish a synchronized session like the kind used in TCP, and UDP doesn\’t guarantee error-free communications. The primary purpose of UDP is to send small packets of information. The application is responsible for acknowledging the correct reception of the dat a. Port 22 is used by both SSH and SCP with UDP. Port 443 is used for secure web connections? HTTPS and is a TCP port. Thus to make sure only the Accounting computer has HTTPS access to the Administrative server you should use TCP port 443 and set the rule to allow communication between 10.4.255.10/24 (Accounting) and 10.4.255.101 (Administrative server1) Thus to make sure that only the HR computer has access to Server2 over SCP you need use of TCP port 22 and set the rule to allow communication between 10.4.255.10/23 (HR) and
10.4.255.2 (server2) Thus to make sure that the IT computer can access both the Administrative servers you need to use a port and accompanying port number and set the rule to allow communication between:
10.4.255.10.25 (IT computer) and 10.4.255.101 (Administrative server1) 10.4.255.10.25 (IT computer) and 10.4.255.102 (Administrative server2)
New Question 13:
You have just received some room and WiFi access control recommendations from a security consulting company. Click on each building to bring up available security controls. Please implement the following requirements:
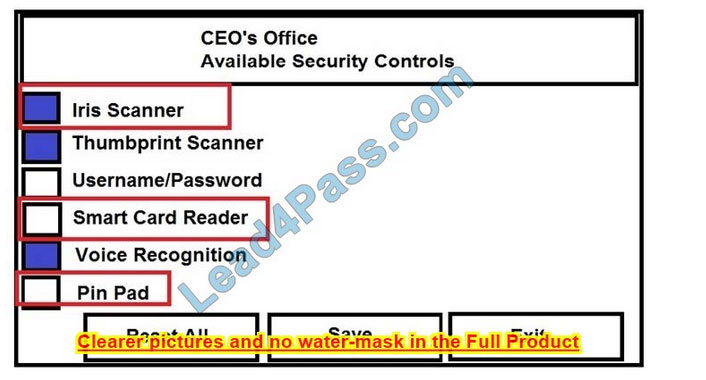
The Chief Executive Officer\’s (CEO) office had multiple redundant security measures installed on the door to the office. Remove unnecessary redundancies to deploy three-factor authentication, while retaining the expensive iris render.
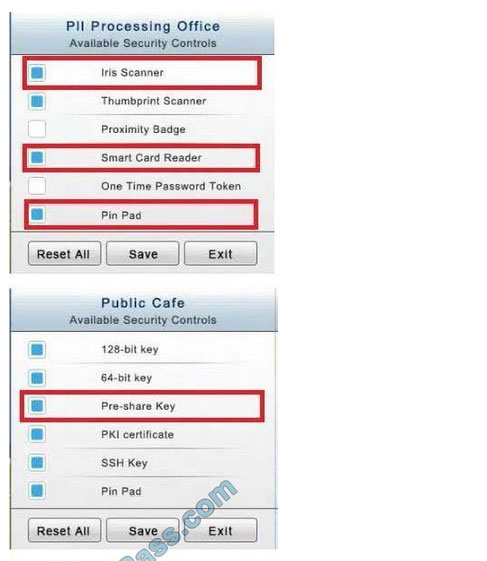
The Public Cafe has wireless available to customers. You need to secure the WAP with WPA and place a passphrase on the customer receipts.
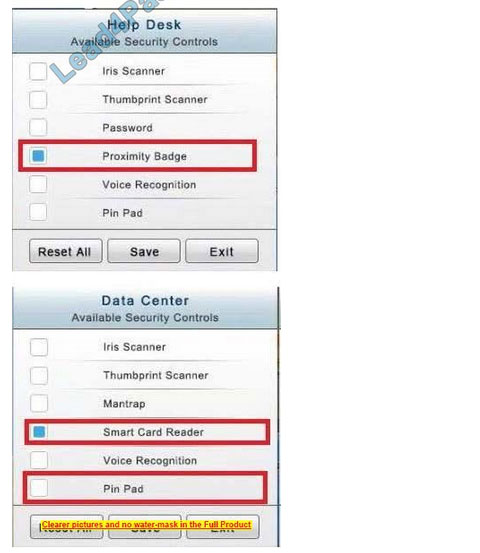
In the Data Center you need to include authentication from the “something you know” category and take advantage of the existing smartcard reader on the door.
In the Help Desk Office, you need to require single factor authentication through the use of physical tokens given to guests by the receptionist.
The PII Office has redundant security measures in place. You need to eliminate the redundancy while maintaining three-factor authentication and retaining the more expensive controls.
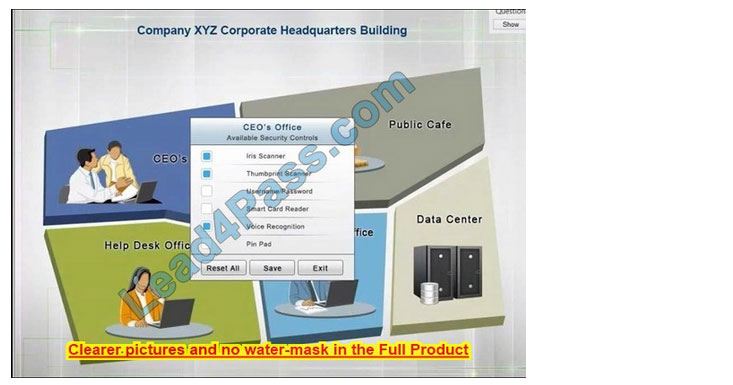
Instructions: The original security controls for each office can be reset at any time by selecting the Reset button. Once you have met the above requirements for each office, select the Save button. When you have completed the entire simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
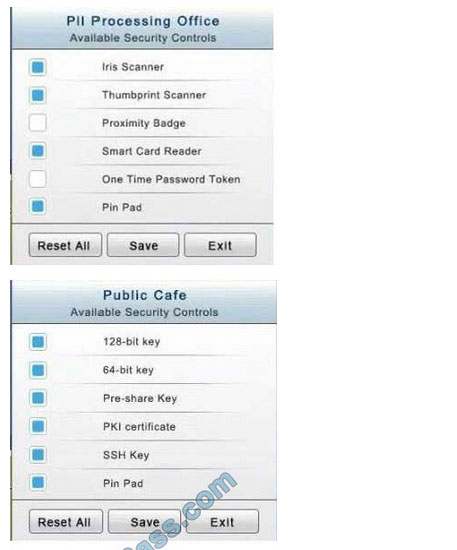
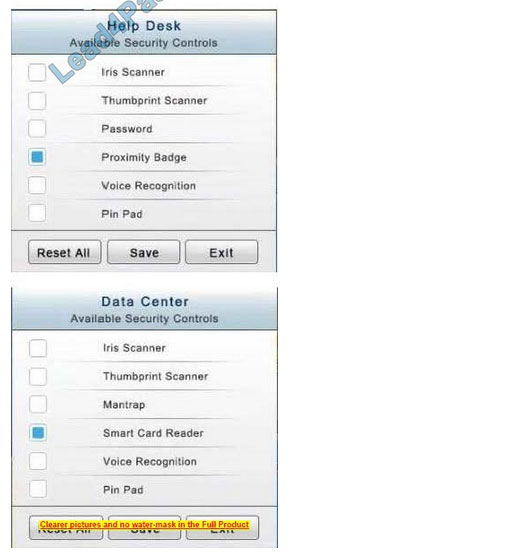

Correct Answer:
See the solution below.
New Question 14:
CORRECT TEXT
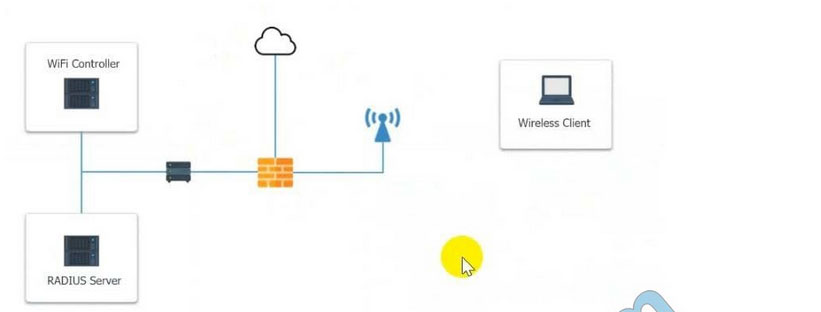
A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
Perform the following slops:
1.
Configure the RADIUS server.
2.
Configure the WiFi controller.
3.
Preconfigure the client for an incoming guest. The guest AD credentials are:
User: guest01 Password: guestpass
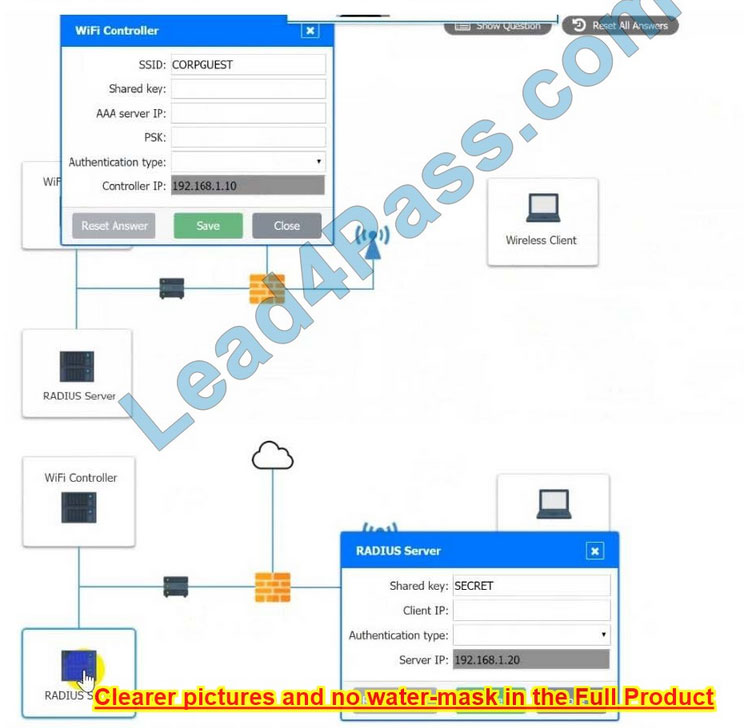
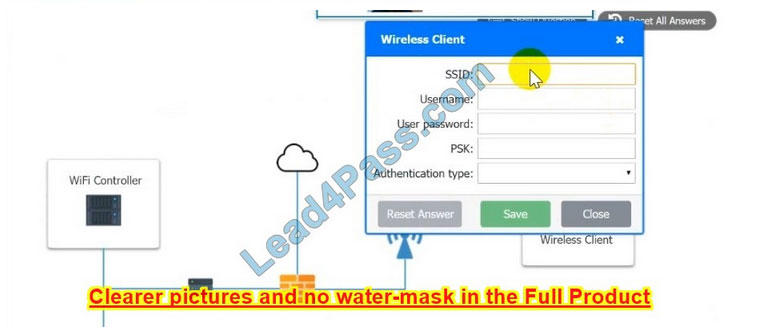
Correct Answer:
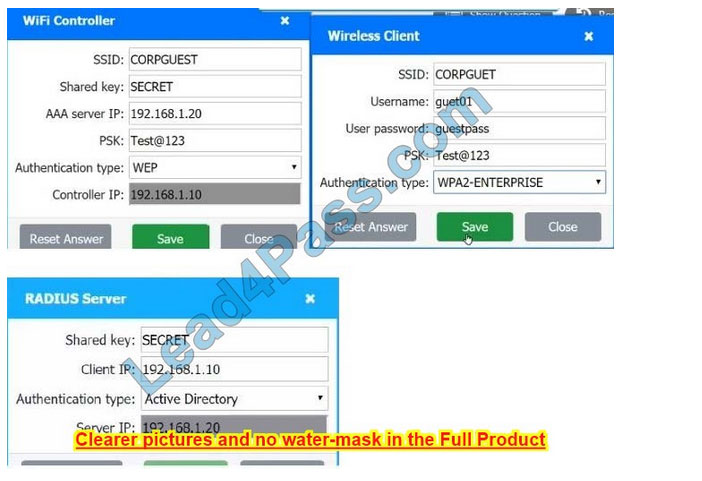
See the answer below.
Use the same settings as describe in below images.
New Question 15:
CORRECT TEXT
An incident has occurred in the production environment.
Analyze the command outputs and identify the type of compromise.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
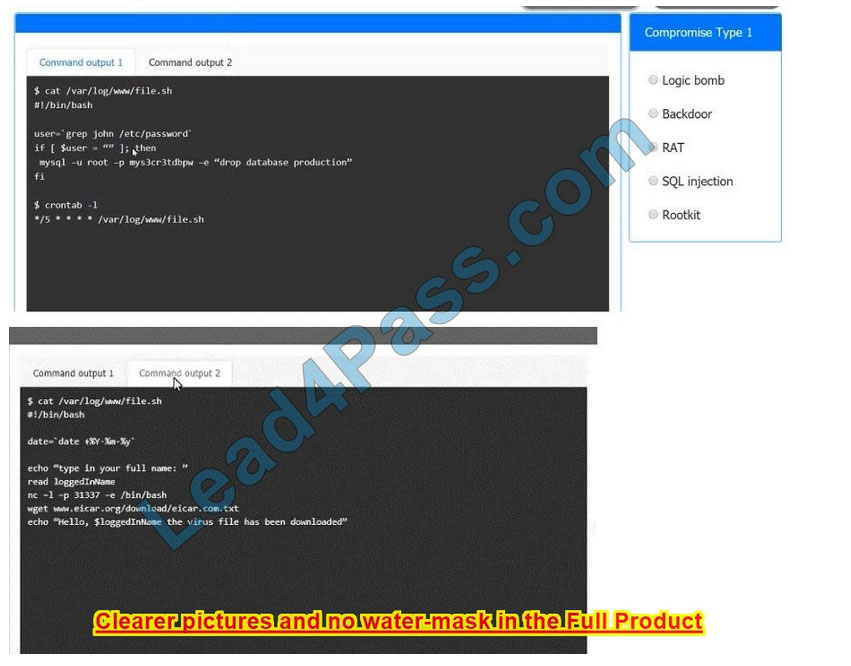
Correct Answer:
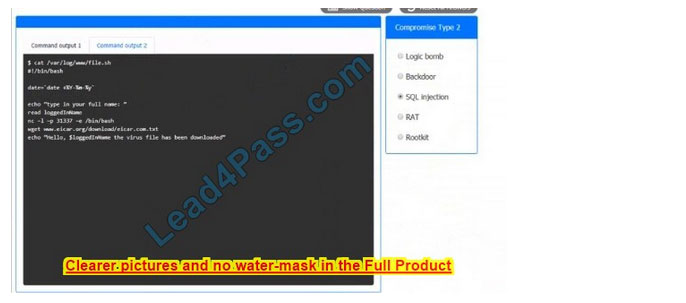
…
Check out the CompTIA sy0-601 PDF available free of charge in 2022:
https://drive.google.com/file/d/1-3cH41u_Mx_ZGHfP6rRjkzrk0lexWpY_/
https://drive.google.com/file/d/15yTMzIypZ64KRobr5X7Bu9fuOx5oneHL/
https://drive.google.com/file/d/1lJ911sJMs1cOPYD3MCKznr89c5s5KTn5/
https://drive.google.com/file/d/1_ij2vKQ_V5lWRMAfyPhC_vzDXyIPfzHI/
Get more CompTIA Sy0-601 dumps: https://www.leads4pass.com/sy0-601.html (Total Questions: 735 Q&A)
CompTIA SY0-601 is a brand new field, and get the latest opportunities through exams. Free content comes as part of the Lead4Pass CompTIA It certification exam. Help you improve your exam experience. Lead4Pass has a success rate of over 99%, helping you pass the exam easily.