Article overview
- Basic information about the CompTIA Security+ SY0-701 exam
- How to pass the CompTIA Security+ SY0-701 exam
- CompTIA Security+ SY0-701 FAQs
The CompTIA Security+ SY0-701 exam is the latest version of the globally recognized certification for cybersecurity professionals.
What are the essential details to know for the 2025 CompTIA Security+ SY0-701 exam? For example, Exam Overview, Exam Format, Exam Domains and Weighting, and the latest practice questions for exam preparation,etc.
Below is a comprehensive overview of the key details you need to know for the 2025 exam:
Exam Overview
- Certification Name: CompTIA Security+
- Exam Code: SY0-701
- Release Date: November 7, 2023 (still active in 2025)
- Purpose: Validates foundational cybersecurity skills and knowledge for roles like security analyst, network administrator, and IT auditor.
Exam Format,Cost and Registration
- Number of Questions: Maximum of 90 questions
- Question Types: Multiple-choice and performance-based questions (e.g., simulations to test practical skills)
- Duration: 90 minutes
- Passing Score: 750 (on a scale of 100-900)
- Languages: English, with additional languages like Japanese, Portuguese, and Spanish available in some regions
- Delivery: Pearson VUE testing centers or online proctored exams
- Exam Fee: Approximately $392 USD (prices may vary by region; check CompTIA’s website for exact costs).
- Vouchers and Discounts: Available through CompTIA’s marketplace, training providers, or academic programs.
- Registration: Schedule via Pearson VUE (www.pearsonvue.com/comptia).
Exam Domains and Weighting
The SY0-701 exam is organized into five domains, reflecting current cybersecurity trends:
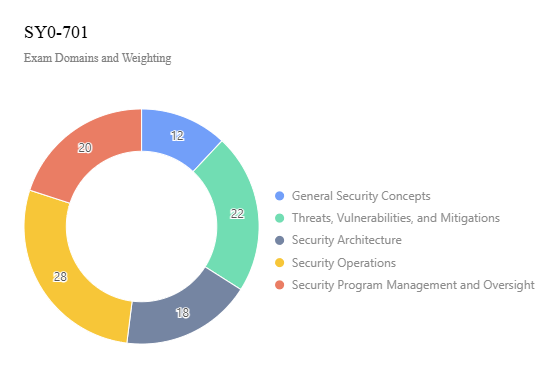
1.General Security Concepts (12%)
Covers foundational security principles, zero trust, and risk management.
2.Threats, Vulnerabilities, and Mitigations (22%)
Focuses on identifying and mitigating threats like malware, social engineering, and network attacks.
3.Security Architecture (18%)
Includes cloud security, network design, and secure system configurations.
4.Security Operations (28%)
Emphasizes monitoring, incident response, and security controls implementation.
5.Security Program Management and Oversight (20%)
Covers governance, compliance, and security policies.
Key Updates in SY0-701 (Compared to SY0-601)
- Increased Focus on Modern Threats: More emphasis on cloud security, IoT vulnerabilities, and hybrid environments.
- Zero Trust and Automation: Greater coverage of zero-trust architecture and automated security tools.
- Hands-On Skills: Performance-based questions test practical abilities in configuring firewalls, analyzing logs, and responding to incidents.
- Emerging Technologies: Includes topics like AI-driven threats and quantum computing risks.
CompTIA has provided a recommendation, slightly adjusting the prerequisites for the Security+ exam. They suggest obtaining the Network+ certification and having two years of experience as a security/systems administrator before taking the SY0-701 exam.
The most important thing is how do we pass the SY0-701 exam?
For candidates preparing for the CompTIA Security+ SY0-701 exam, it’s not only essential to understand all the basic exam information, but knowing how to pass the exam is the most critical. In addition to mastering foundational knowledge, effective practice tests are highly necessary, as they can significantly improve the pass rate. Leads4Pass SY0-701 dumps have been recently updated with 718 exam questions and answers to help you practice effectively and achieve a high score to pass the CompTIA Security+ SY0-701 exam.
Get the latest SY0-701 dumps at https://www.leads4pass.com/sy0-701.html, and choose either PDF or VCE simulation engine to help you prepare with ease.
You are welcome to first take the CompTIA Security+ SY0-701 online practice test.
The latest CompTIA Security+ SY0-701 exam questions and answers
| Number of exam questions | Download |
| 15 Q&As (Free) | SY0-701 Dumps PDF |
Question 1:
A security team is reviewing the findings in a report that was delivered after a third party performed a penetration test. One of the findings indicated that a web application form field is vulnerable to cross-site scripting. Which of the following application security techniques should the security analyst recommend the developer implement to prevent this vulnerability?
A. Secure cookies
B. Version control
C. Input validation
D. Code signing
Correct Answer: C
Input validation is a technique that checks the user input for any malicious or unexpected data before processing it by the web application.
Input validation can prevent cross-site scripting (XSS) attacks, which exploit the vulnerability of a web application to execute malicious scripts in the browser of a victim. XSS attacks can compromise the confidentiality, integrity, and availability of the web application and its users.
Input validation can be implemented on both the client-side and the server-side, but server-side validation is more reliable and secure. Input validation can use various methods, such as whitelisting, blacklisting, filtering, escaping, encoding, and sanitizing the input data.
References: CompTIA Security+ Study Guide with over 500 Practice Test Questions: Exam SY0-701, 9th Edition, Chapter 2, page 70. CompTIA Security+ (SY0-701) Certification Exam Objectives, Domain 3.2, page 11. Application Security SY0-601 CompTIA Security+ : 3.2
Question 2:
A company is required to perform a risk assessment on an annual basis. Which of the following types of risk assessments does this requirement describe?
A. Continuous
B. Ad hoc
C. Recurring
D. One time
Correct Answer: C
Question 3:
A security analyst is investigating an alert that was produced by endpoint protection software. The analyst determines this event was a false positive triggered by an employee who attempted to download a file. Which of the following is the most likely reason the download was blocked?
A. A misconfiguration in the endpoint protection software
B. A zero-day vulnerability in the file
C. A supply chain attack on the endpoint protection vendor
D. Incorrect file permissions
Correct Answer: A
The most likely reason the download was blocked, resulting in a false positive, is a misconfiguration in the endpoint protection software. False positives occur when legitimate actions are incorrectly identified as threats due to incorrect settings or overly aggressive rules in the security software.
Misconfiguration in the endpoint protection software: Common cause of false positives, where legitimate activities are flagged incorrectly due to improper settings. Zero-day vulnerability: Refers to previously unknown vulnerabilities, which are
less likely to be associated with a false positive. Supply chain attack: Involves compromising the software supply chain, which is a broader and more severe issue than a simple download being blocked. Incorrect file permissions: Would prevent access to files but not typically cause an alert in endpoint protection software.
Reference: CompTIA Security+ SY0-701 Exam Objectives, Domain 4.3 – Explain various activities associated with vulnerability management (False positives).
Question 4:
Which of the following should a security operations center use to improve its incident response procedure?
A. Playbooks
B. Frameworks
C. Baselines
D. Benchmarks
Correct Answer: A
A playbook is a documented set of procedures that outlines the step-by-step response to specific types of cybersecurity incidents. Security Operations Centers (SOCs) use playbooks to improve consistency, efficiency, and accuracy during incident response.
Playbooks help ensure that the correct procedures are followed based on the type of incident, ensuring swift and effective remediation. Frameworks provide general guidelines for implementing security but are not specific enough for incident response procedures.
Baselines represent normal system behavior and are used for anomaly detection, not incident response guidance.
Benchmarks are performance standards and are not directly related to incident response.
Question 5:
After conducting a vulnerability scan, a systems administrator notices that one of the identified vulnerabilities is not present on the systems that were scanned. Which of the following describes this example?
A. False positive
B. False negative
C. True positive
D. True negative
Correct Answer: A
A false positive occurs when a vulnerability scan identifies a vulnerability that is not actually present on the systems that were scanned. This means that the scan has incorrectly flagged a system as vulnerable.
False positive: Incorrectly identifies a vulnerability that does not exist on the scanned systems.
False negative: Fails to identify an existing vulnerability on the system. True positive: Correctly identifies an existing vulnerability. True negative: Correctly identifies that there is no vulnerability.
Reference: CompTIA Security+ SY0-701 Exam
Objectives, Domain 4.3 – Explain various activities associated with vulnerability management (False positives and false negatives).
Question 6:
The Chief Information Security Officer (CISO) at a large company would like to gain an understanding of how the company\’s security policies compare to the requirements imposed by external regulators. Which of the following should the CISO use?
A. Penetration test
B. Internal audit
C. Attestation
D. External examination
Correct Answer: D
An external examination (also known as an external audit or external review) is the best method for the Chief Information Security Officer (CISO) to gain an understanding of how the company\’s security policies compare to external regulatory requirements.
External examinations are conducted by third-party entities that assess an organization\’s compliance with laws, regulations, and industry standards. Penetration tests focus on identifying vulnerabilities, not compliance. Internal audits assess internal controls but are not impartial or focused on regulatory requirements.
Attestation is a formal declaration but does not involve the actual evaluation of compliance.
Question 7:
Which of the following best practices gives administrators a set period to perform changes to an operational system to ensure availability and minimize business impacts?
A. Impact analysis
B. Scheduled downtime
C. Backout plan
D. Change management boards
Correct Answer: B
Scheduled downtime is a planned period of time when a system or service is unavailable for maintenance, updates, upgrades, or other changes.
Scheduled downtime gives administrators a set period to perform changes to an operational system without disrupting the normal business operations or affecting the availability of the system or service. Scheduled downtime also allows administrators to inform the users and stakeholders about the expected duration and impact of the changes.
References:
CompTIA Security+ Study Guide: Exam SY0-701, 9th Edition, Chapter 12: Security Operations and Administration, page 579 1
Question 8:
Which of the following would be most useful in determining whether the long-term cost to transfer a risk is less than the impact of the risk?
A. ARO
B. RTO
C. RPO
D. ALE
E. SLE
Correct Answer: D
Question 9:
Which of the following describes the process of concealing code or text inside a graphical image?
A. Symmetric encryption
B. Hashing
C. Data masking
D. Steganography
Correct Answer: D
Steganography is the process of hiding information within another medium, such as an image, audio, video, or text file. The hidden information is not visible or noticeable to the casual observer, and can only be extracted by using a specific technique or key. Steganography can be used for various purposes, such as concealing secret messages, watermarking, or evading detection by antivirus software12
References:
1: CompTIA Security+ Study Guide: Exam SY0-701, 9th Edition, Chapter 5: Cryptography and PKI, page 233 2: CompTIA Security+ Certification Kit: Exam SY0-701, 7th Edition, Chapter 5: Cryptography and PKI, page 235
Question 10:
Which of the following vulnerabilities is associated with installing software outside of a manufacturer\’s approved software repository?
A. Jailbreaking
B. Memory injection
C. Resource reuse
D. Side loading
Correct Answer: D
Side loading is the process of installing software outside of a manufacturer\’s approved software repository. This can expose the device to potential vulnerabilities, such as malware, spyware, or unauthorized access.
Side loading can also bypass security controls and policies that are enforced by the manufacturer or the organization. Side loading is often done by users who want to access applications or features that are not available or allowed on their devices.
References: Sideloading – CompTIA Security + Video Training | Interface Technical Training, Security+ (Plus) Certification | CompTIA IT Certifications, Load Balancers -CompTIA Security+ SY0-501 -2.1, CompTIA Security+ SY0-601 Certification Study Guide.
Question 11:
An engineer recently deployed a group of 100 web servers in a cloud environment. Per the security policy, all web-server ports except 443 should be disabled. Which of the following can be used to accomplish this task?
A. Application allow list
B. SWG
C. Host-based firewall
D. VPN
Correct Answer: C
Host-based firewall – This is a firewall on a host where you can configured rules for ports/connections allowed on that specific host.
As the question specifically is asking for web-server ports to be blocked, it would make more sense to configure rules to block the ports on each web server.
========================
Other Choices:
Application allow list – A list of applications and application components that are permitted to reside or perform actions on a device SWG(Secure Web Gateway) – A security product that operates between employees and the internet by filtering unsafe content from web traffic to stop cyber threats and data breaches. They also block risky or unauthorized user behavior.
SWGs usually analyses the content of traffic.
VPN (Virtual Private Network) – A service that establishes a secure encrypted connection between networks over the internet. Hosts connected on the network will behave logically as if they\’re on the same network even if they are a physically not.
Question 12:
A security analyst is investigating an application server and discovers that software on the server is behaving abnormally. The software normally runs batch jobs locally and does not generate traffic, but the process is now generating outbound traffic over random high ports. Which of the following vulnerabilities has likely been exploited in this software?
A. Memory injection
B. Race condition
C. Side loading
D. SQL injection
Correct Answer: A
Memory injection vulnerabilities allow unauthorized code or commands to be executed within a software program, leading to abnormal behavior such as generating outbound traffic over random high ports. This issue often arises from software not properly validating or encoding input, which can be exploited by attackers to inject malicious code.
References:
CompTIA Security+ SY0-701 course content and official CompTIA study resources.
Question 13:
Which of the following is the most effective way to protect an application server running software that is no longer supported from network threats?
A. Air gap
B. Barricade
C. Port security
D. Screen subnet
Correct Answer: A
Air-gapping is the most effective way to protect an application server running unsupported software from network threats.
By physically isolating the server from any network connection (no wired or wireless communication), it is protected from external cyber threats. While other options like port security or a screened subnet can provide some level of protection, an air gap offers the highest level of security by preventing any network- based attacks entirely.
References:
CompTIA Security+ SY0-701 Course Content: Domain 03 Security Architecture. CompTIA Security+ SY0-601 Study Guide: Chapter on Secure System Design.
Question 14:
Which of the following is a common source of unintentional corporate credential leakage in cloud environments?
A. Code repositories
B. Dark web
C. Threat feeds
D. State actors
E. Vulnerability databases
Correct Answer: A
Code repositories are a common source of unintentional corporate credential leakage, especially in cloud environments. Developers may accidentally commit and push sensitive information, such as API keys, passwords, and other credentials, to public or poorly secured repositories. These credentials can then be accessed by unauthorized users, leading to security breaches.
Ensuring that repositories are properly secured and that sensitive data is never committed is critical for protecting against this type of leakage.
References:
CompTIA Security+ SY0-701 Course Content: Domain 03 Security Architecture. CompTIA Security+ SY0-601 Study Guide: Chapter on Threats and Vulnerability Management.
Question 15:
Which of the following is the best reason to complete an audit in a banking environment?
A. Regulatory requirement
B. Organizational change
C. Self-assessment requirement
D. Service-level requirement
Correct Answer: A
A regulatory requirement is a mandate imposed by a government or an authority that must be followed by an organization or an individual. In a banking environment, audits are often required by regulators to ensure compliance with laws, standards, and policies related to security, privacy, and financial reporting. Audits help to identify and correct any gaps or weaknesses in the security posture and the internal controls of the organization.
References:
Official CompTIA Security+ Study Guide (SY0-701), page 507 Security+ (Plus) Certification | CompTIA IT Certifications 2.
…
Relying solely on these practice questions is not enough to pass the SY0-701 exam. The latest free CompTIA Security+ SY0-701 dumps and exam practice questions have been shared with you; all you need to do is take action.
Get the latest SY0-701 dumps at https://www.leads4pass.com/sy0-701.html to help you pass the 2025 CompTIA Security+ SY0-701 exam.
Next, you can continue reading other questions most commonly asked by candidates, collected from across the web.
About the 2025 CompTIA SY0-701 FAQs
Here are the frequently asked questions and answers about the CompTIA SY0-701 exam that candidates are concerned about.
CompTIA security+ 701 vaild for?
The CompTIA Security+ SY0-701 certification is valid for three years from the date you pass the exam. To maintain the certification, you must renew it before the expiration date through CompTIA’s Continuing Education (CE) program, which requires earning 50 Continuing Education Units (CEUs) or retaking the exam.
How many PBQs are on security+ 701?
The CompTIA Security+ SY0-701 exam typically includes 1 to 10 performance-based questions (PBQs), with the usual expectation being around 4 to 5 PBQs. These questions appear at the start of the exam and involve solving problems in simulated IT environments, such as configuring firewalls or analyzing logs.
Can I still take the Security+ SY0-601 exam?
No, you can no longer take the CompTIA Security+ SY0-601 exam, as it was retired on July 31, 2024, for the English-language version. The SY0-601 exam has been replaced by the current version, SY0-701, which was released on November 7, 2023.
Finally, I’d like to say:
Thank you for reading. I spent an entire day collecting truly useful SY0-701 exam information from across the web, combined with my accumulated content, as well as the latest exam questions and answers provided by Leads4Pass, to share with you. If you find it helpful, please bookmark and share.